Microsoft Ignite Day 0 Live Blog: Pre-Day Session: Mastering Cloud Strategy: Deploy and Manage Windows 365
Hello from Microsoft Ignite in San Francisco. Today was Microsoft Ignite Day 0, pre-day sessions were held and I attended Mastering Cloud Strategy: Deploy and Manage Windows 365. I live blogged the experience, and below are my notes and insights from the session. I’ve also updated the post to include the slide-deck from the session. I did miss a few slides, but most of them should be here.
I will likely be making more advanced posts on some of these features oef Windows 365 in the near future as well to cover some of this in more detail. Stay tuned for the rest of this week for more information and announcements from Microsoft Ignite 2025!
1. Session Opening & Key Announcements
Scott Manchester opened with a keynote.
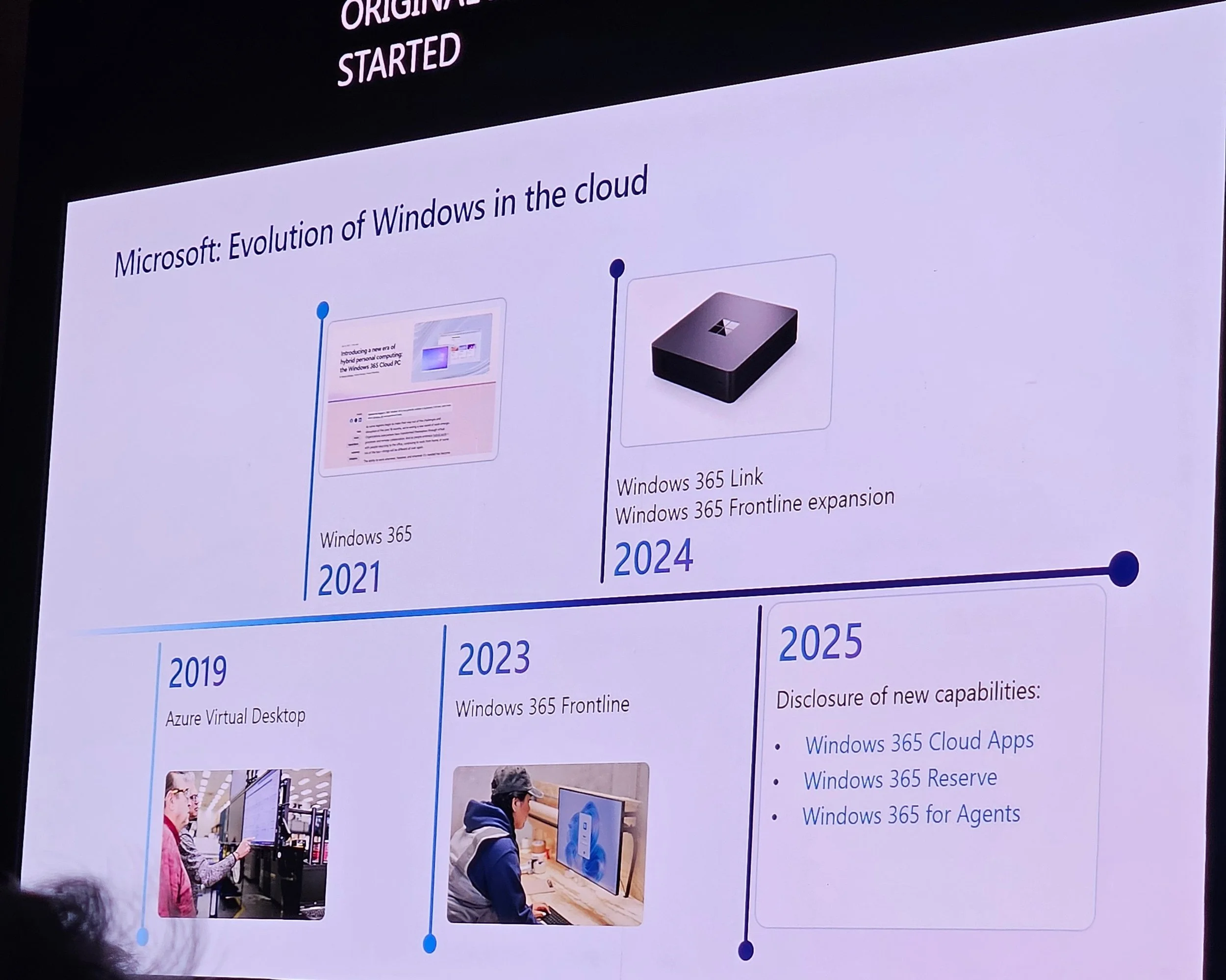
Timeline: Azure Virtual Desktop (2019), Windows 365 (2021), Windows 365 Link (2024).
Windows 365 Link: Fast provisioning (~2.5 minutes), Intune-enrolled, high security.
New for 2025: Windows 365 Cloud Apps, Reserve, and Agents.
Reserve pricing to be announced at Ignite.
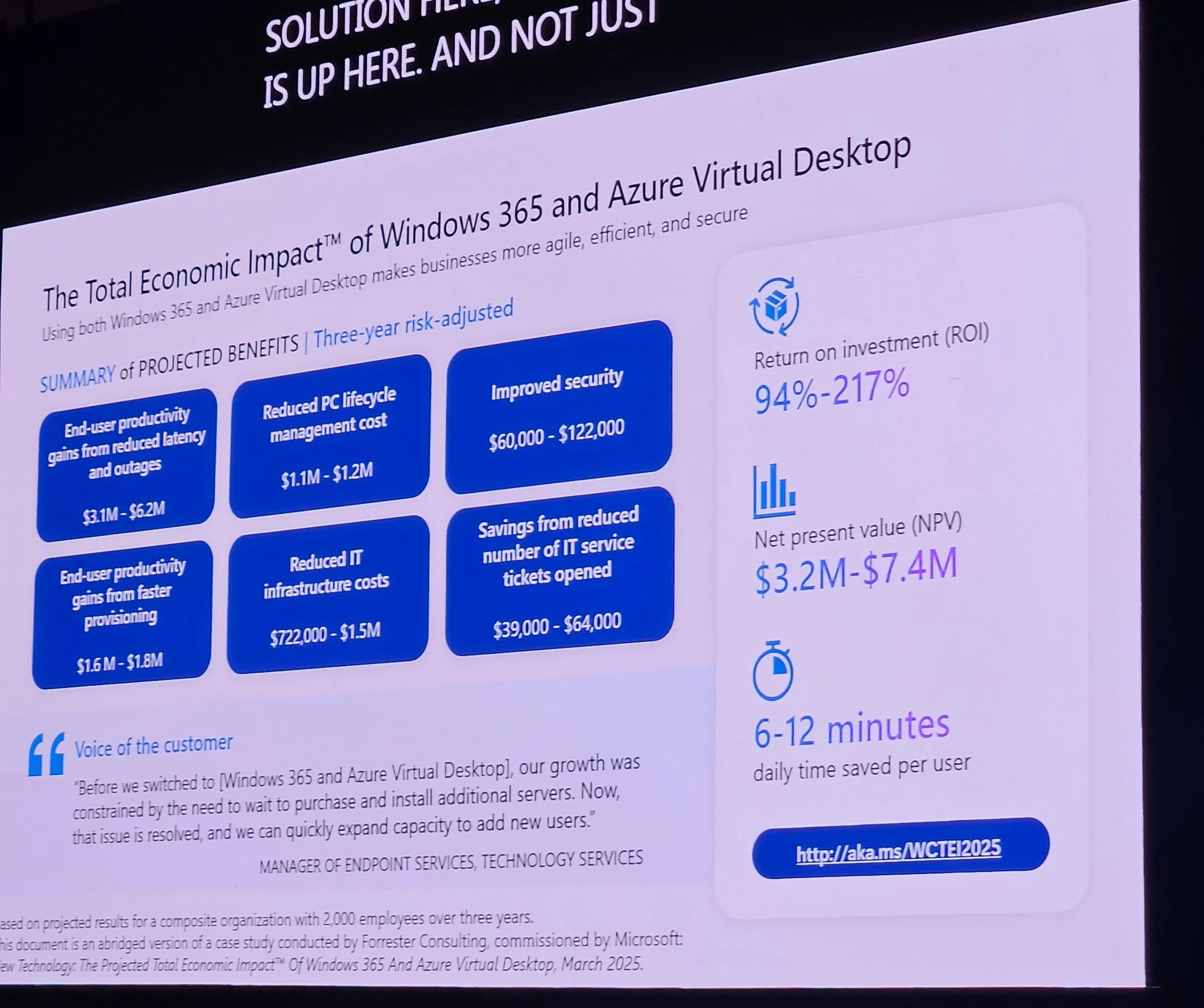
Users save 6–12 minutes daily on average with Windows 365.
Disaster recovery: Cross-region restore and DR Plus features.
2. Windows 365 Overview & Licensing
Christine Gerth presented licensing and experience types:
Enterprise: Dedicated PC per user.
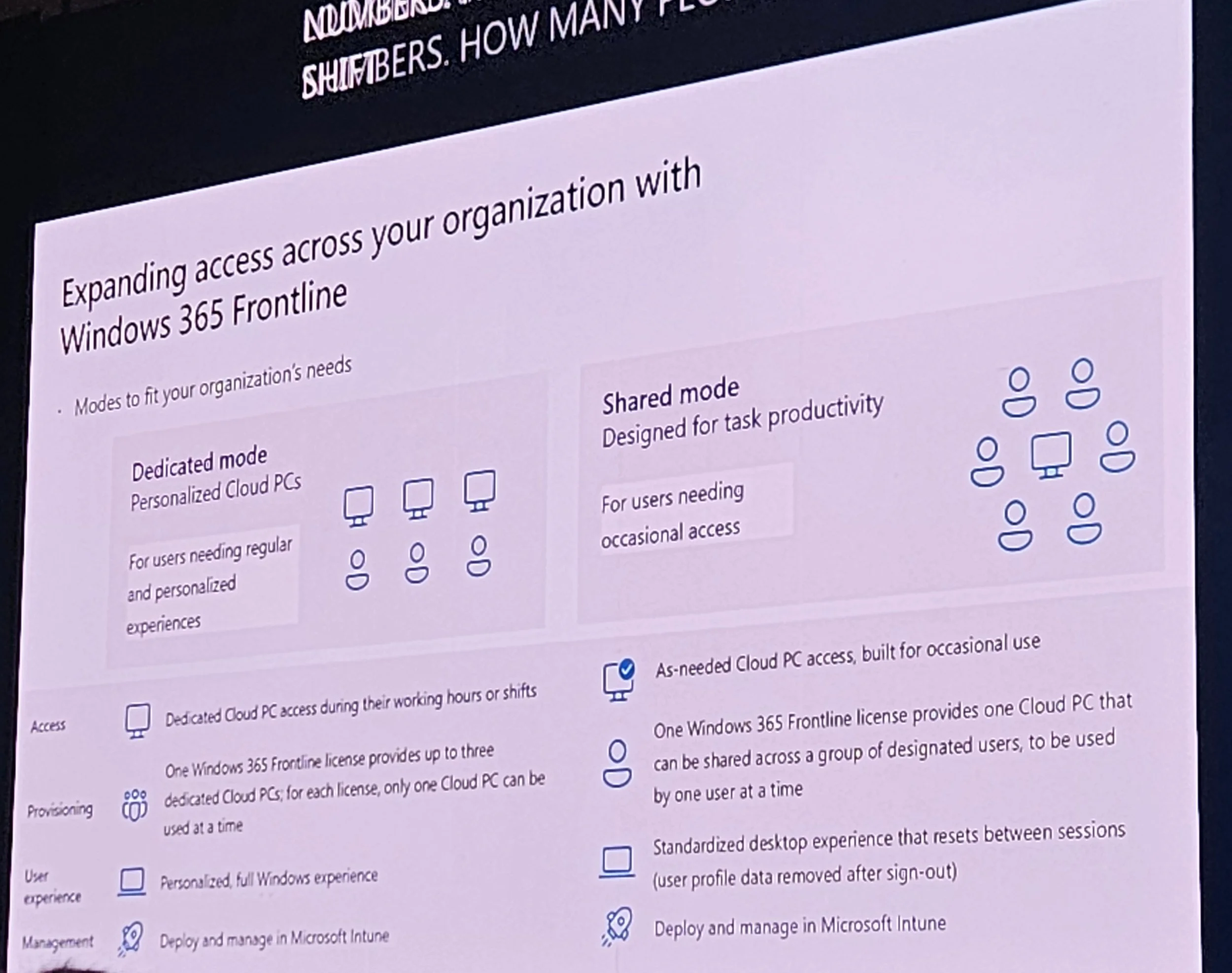
Frontline Dedicated: Multiple users, one at a time.
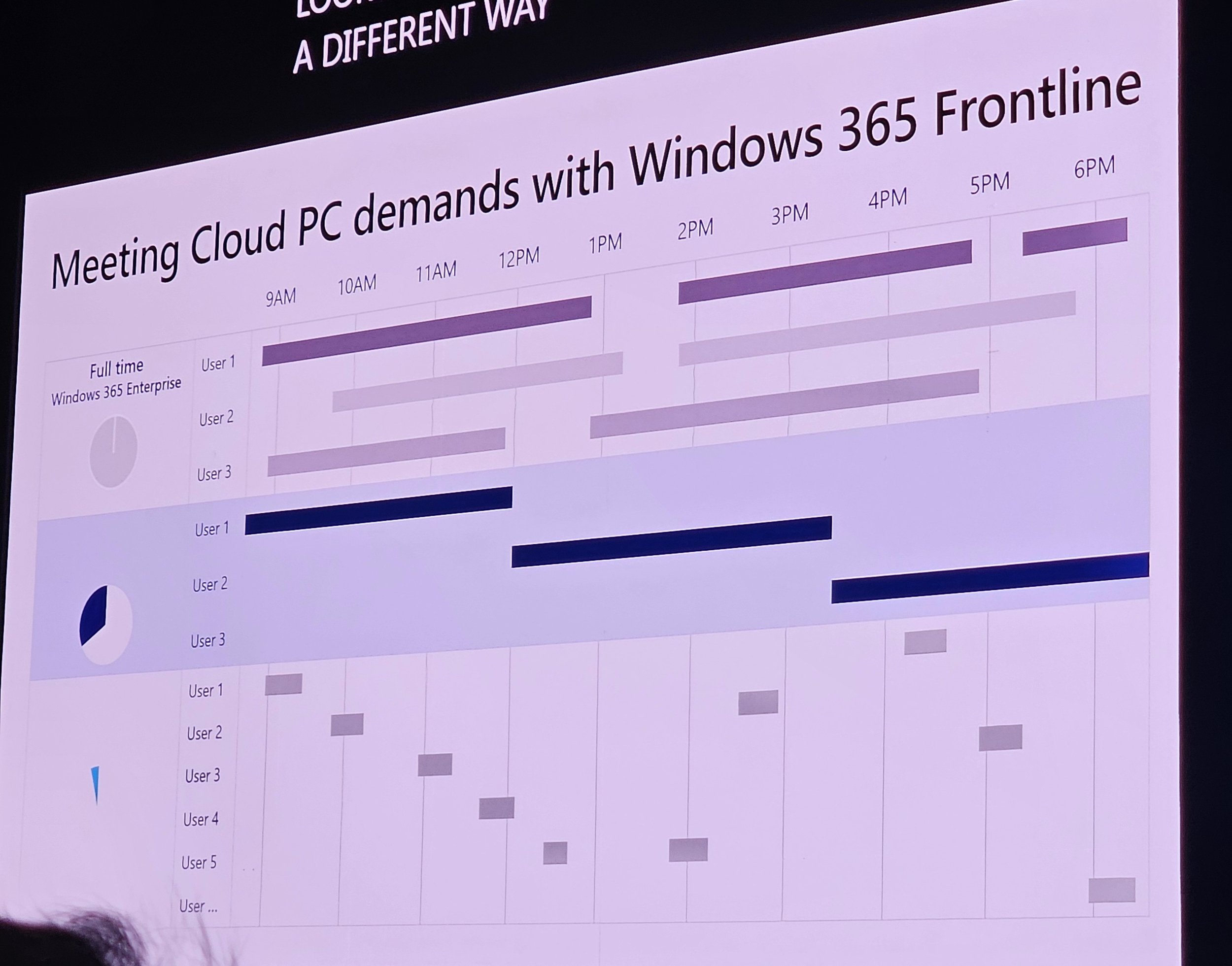
Frontline Shared: Pool of temporary devices.
Cloud Apps (preview): App-only access, not full device.
Dedicated mode: Ideal for shift work groups.
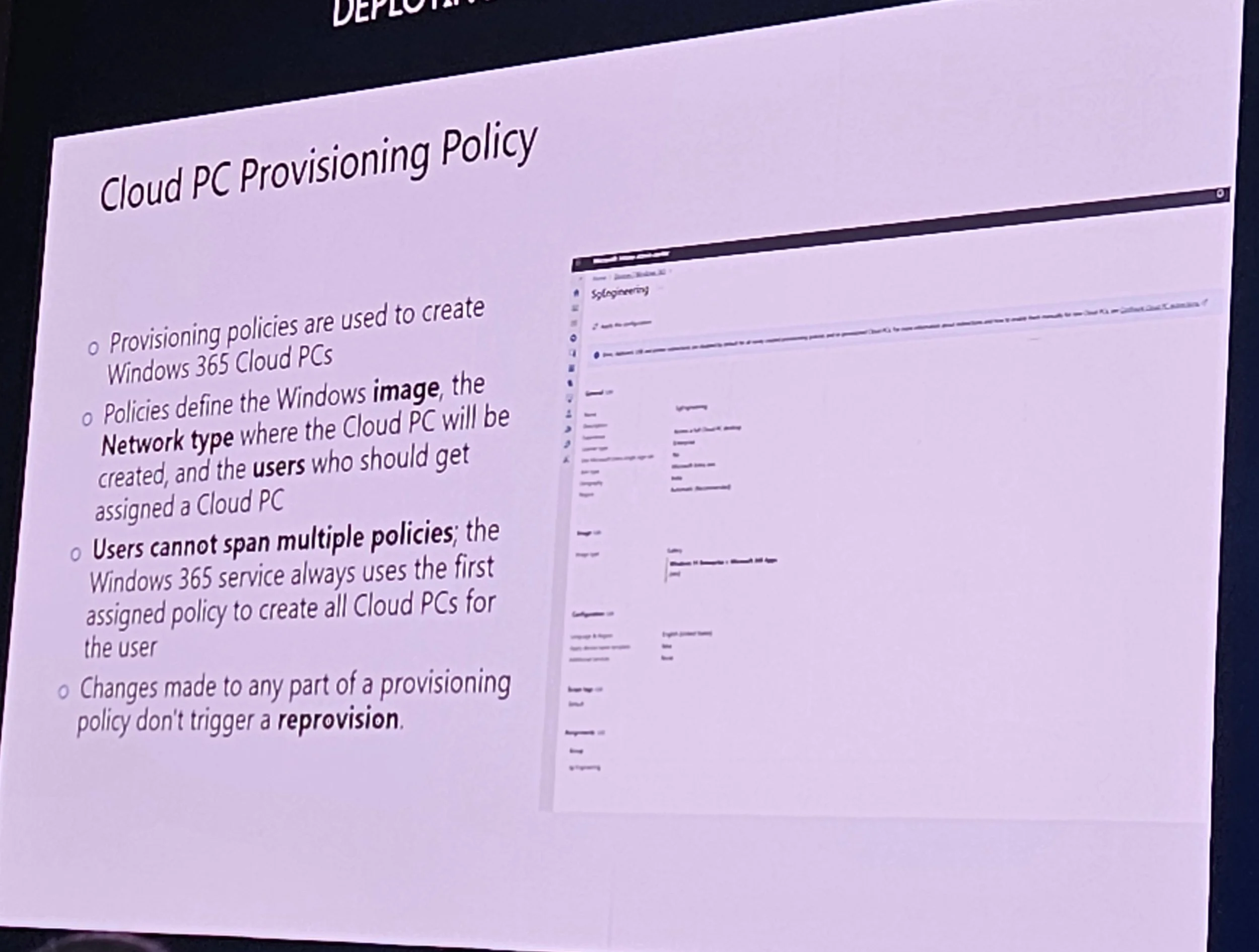
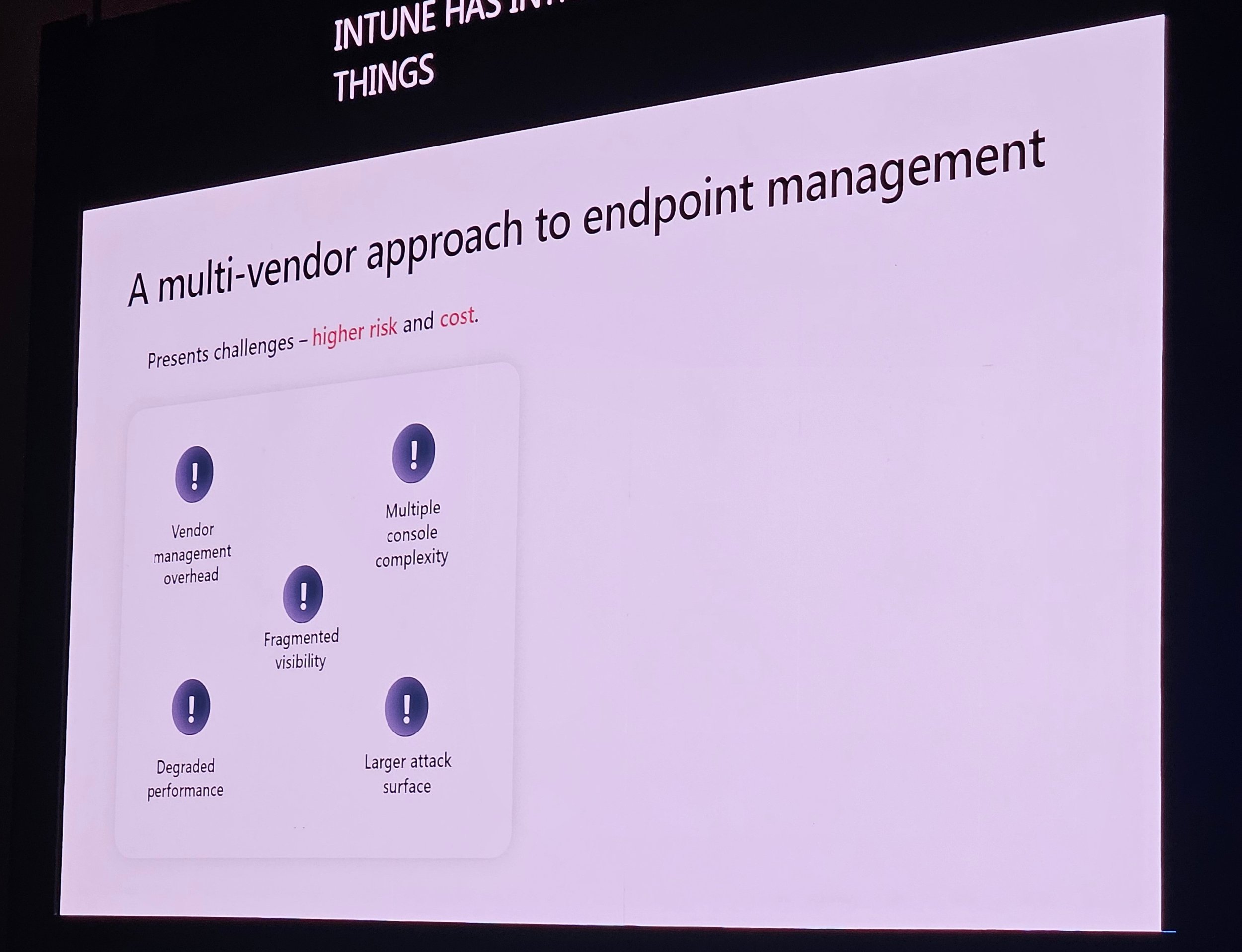
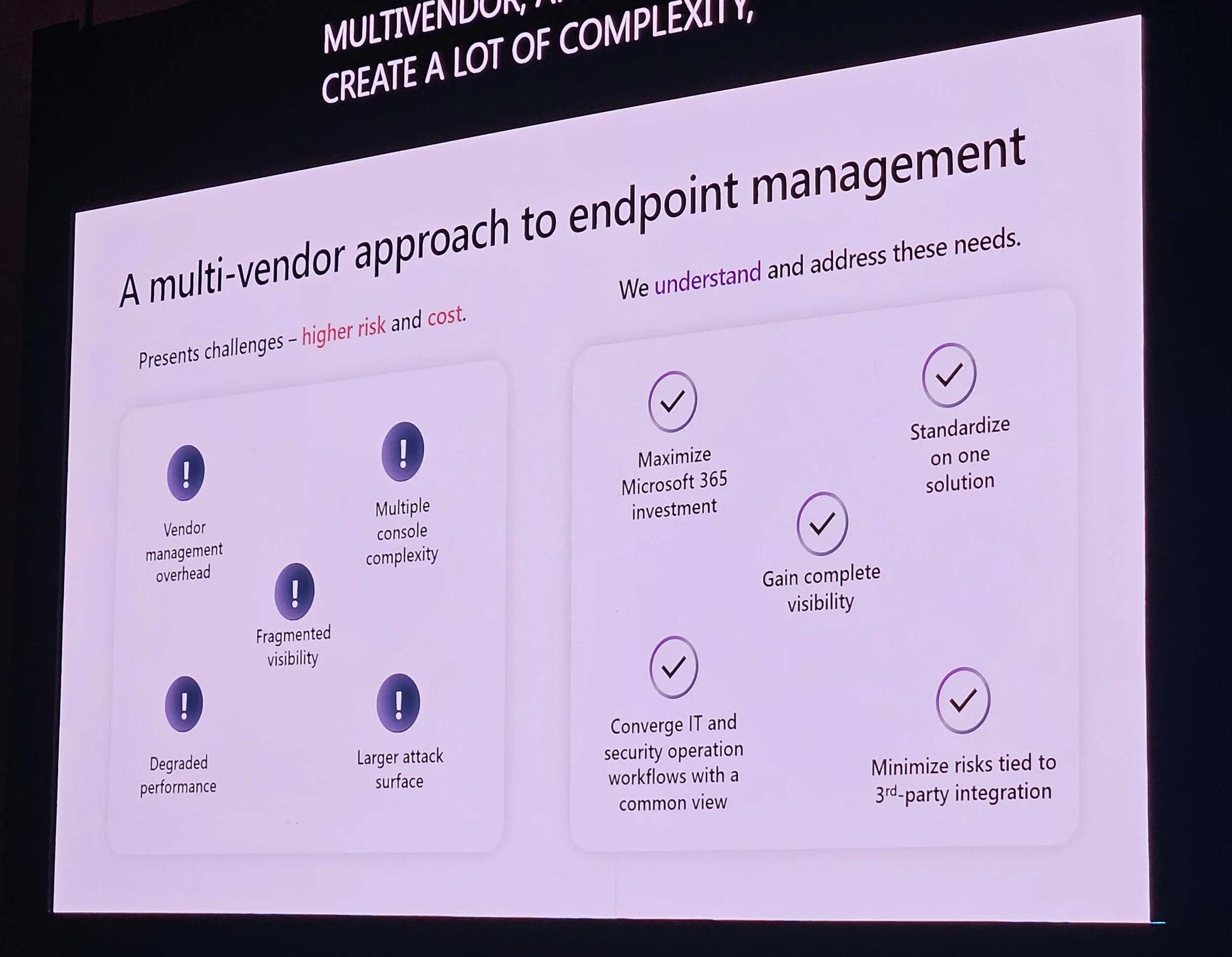
3. Provisioning & Deployment Strategies
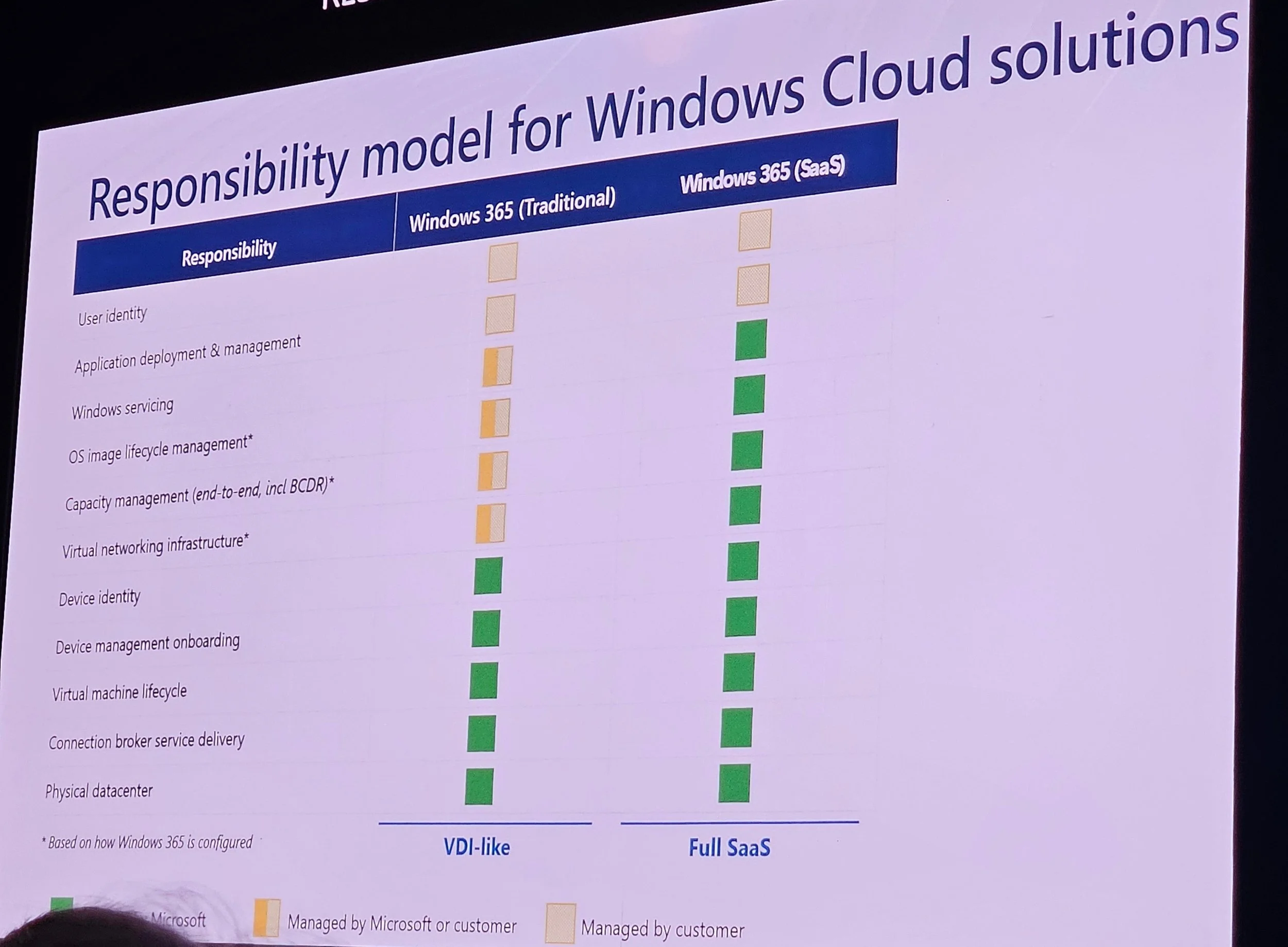
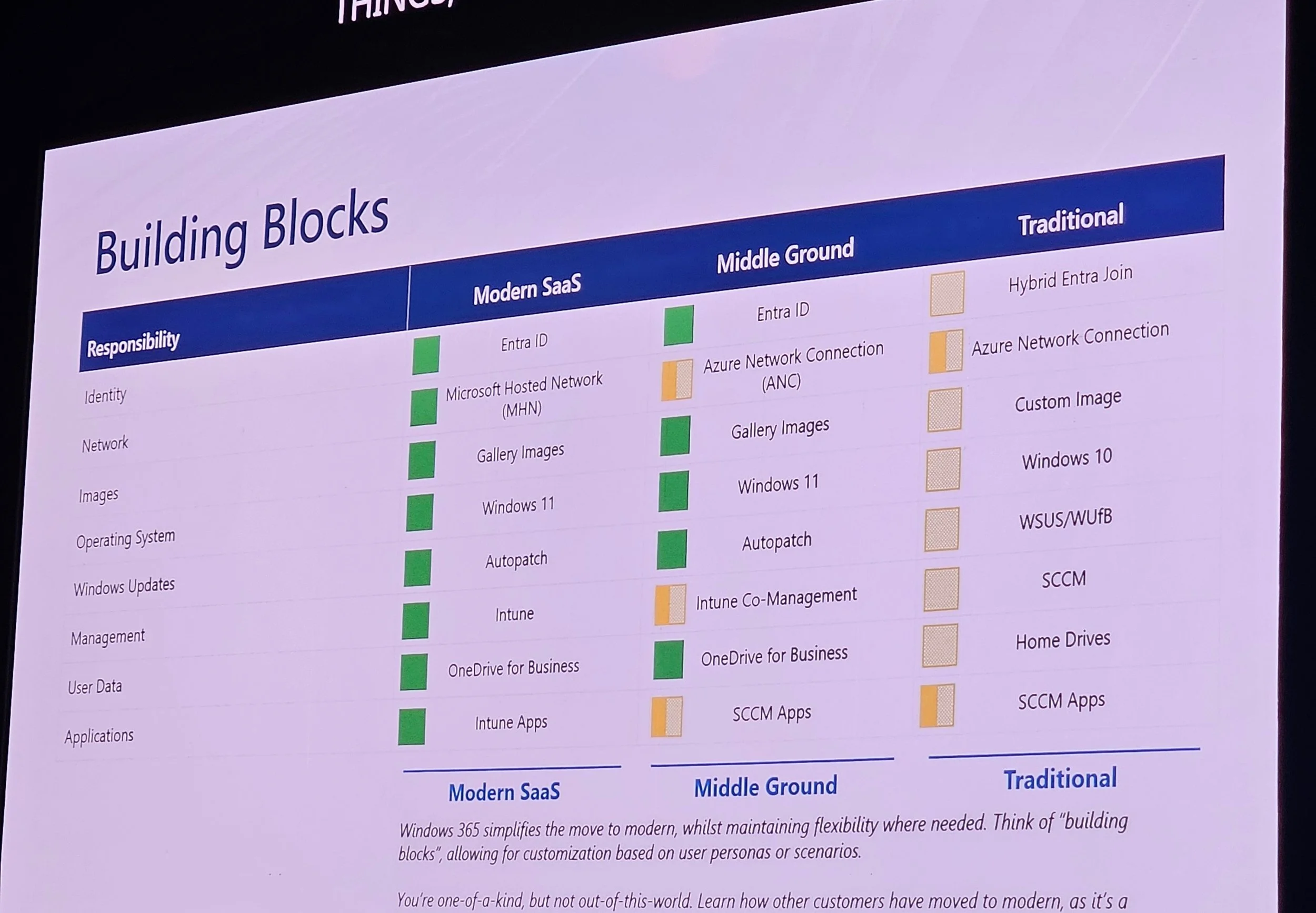
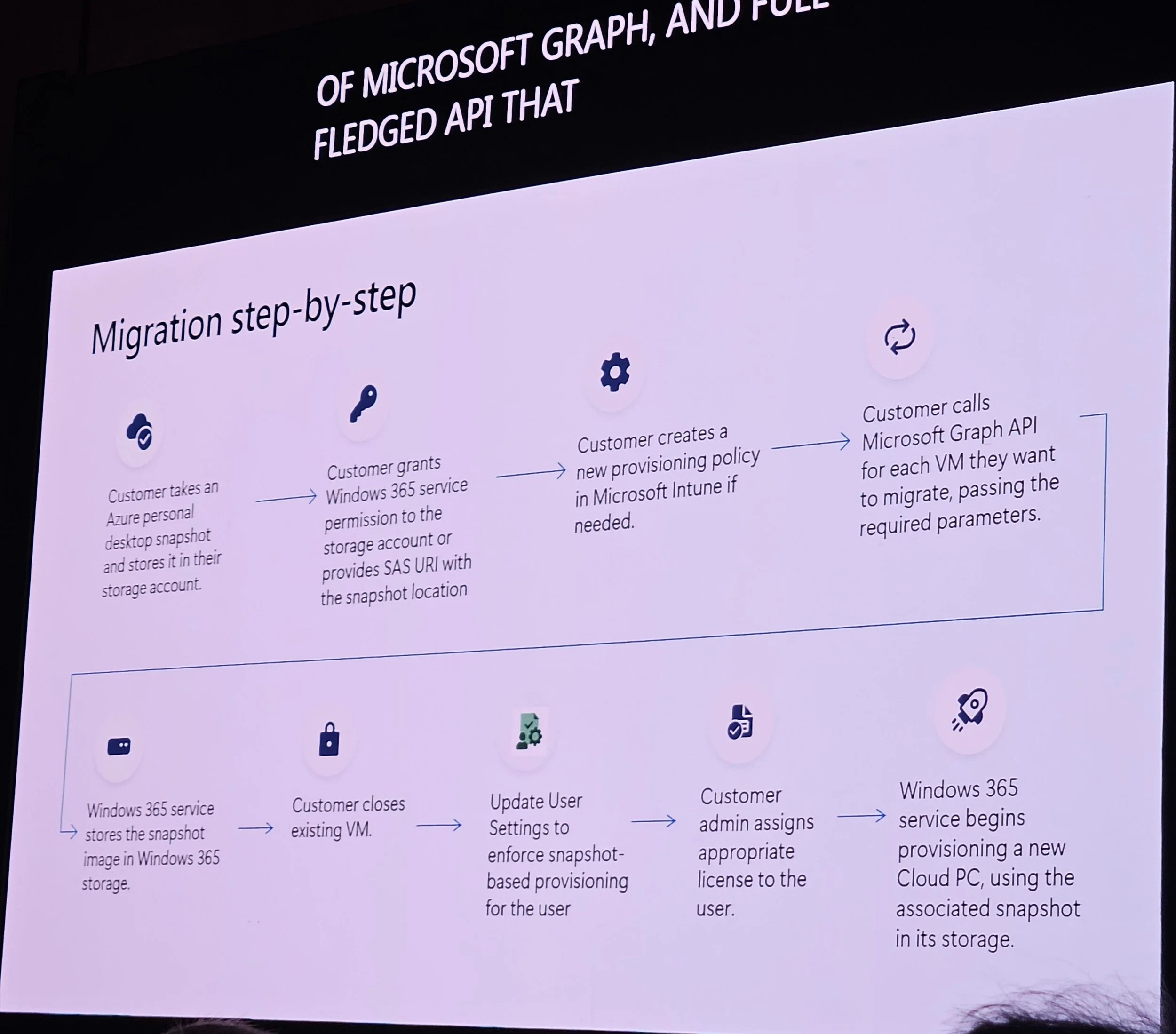
Steve Thomas discussed transforming VDI into SaaS.
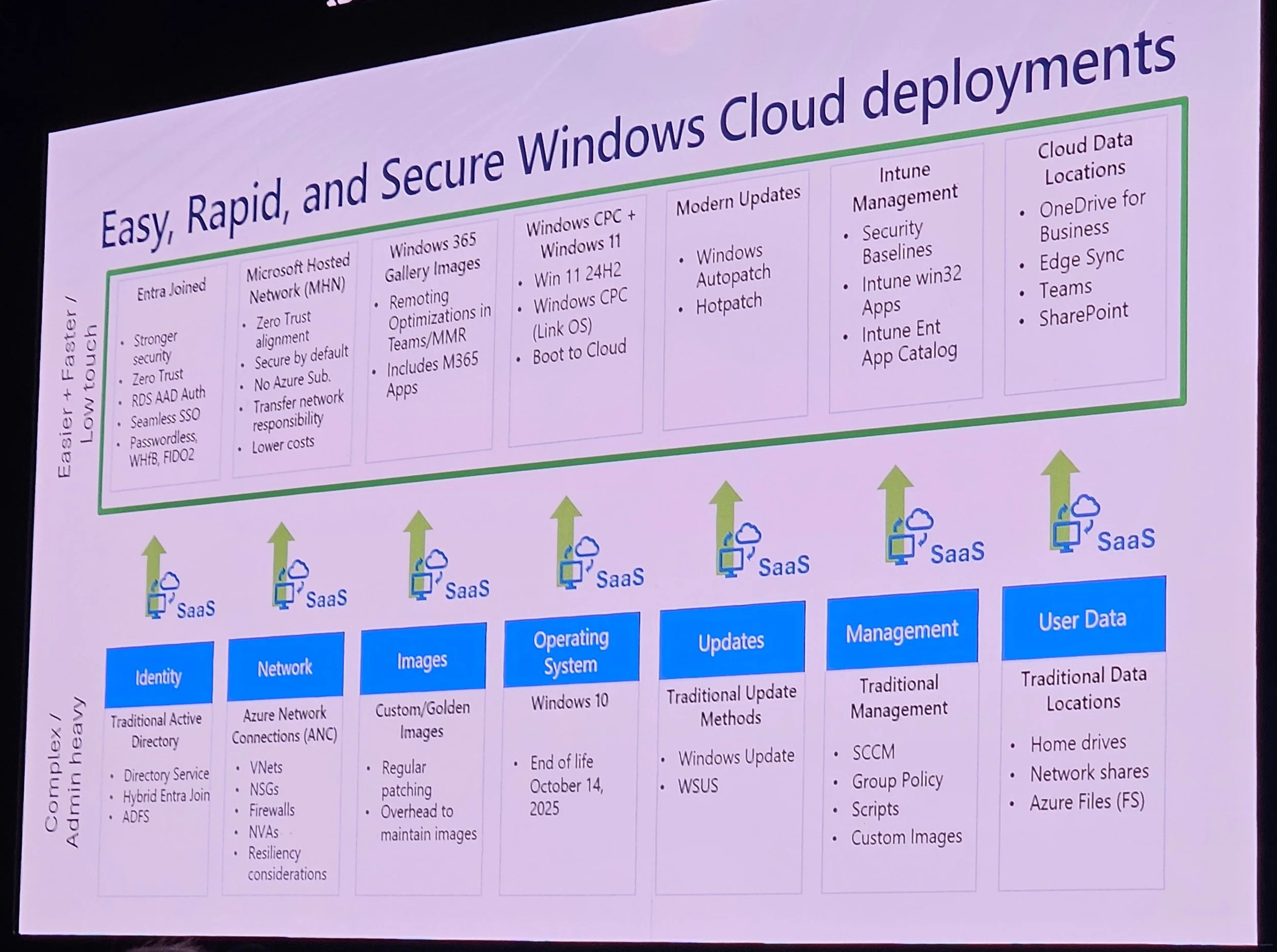
Azure subscription and resources per region are optional but useful.
Intune is central; ConfigMgr and on-prem resources are less necessary.
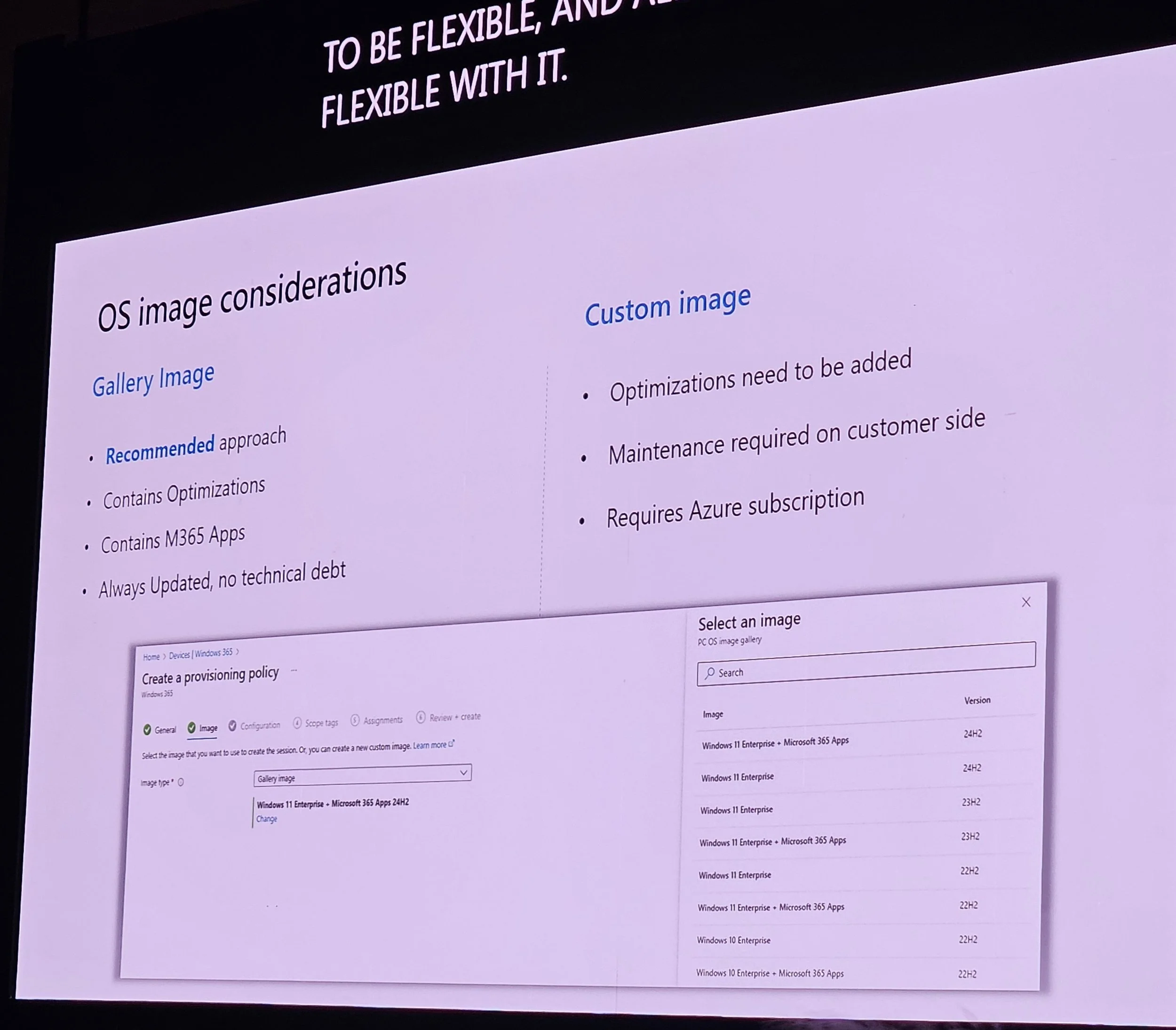
Image management: Gallery images recommended (optimized, updated, no technical debt).
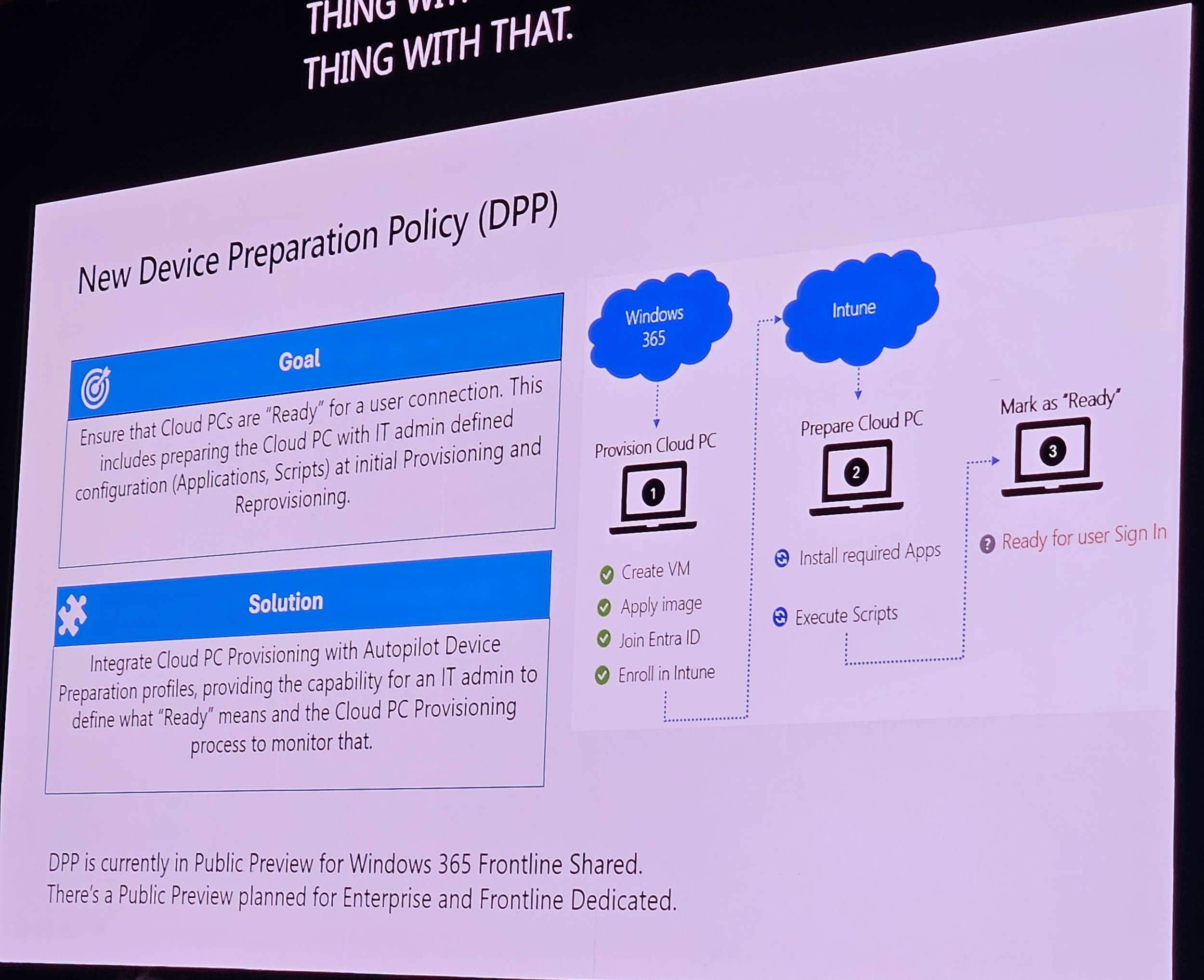
Device Preparation Policy (DPP) in preview for Frontline Shared.
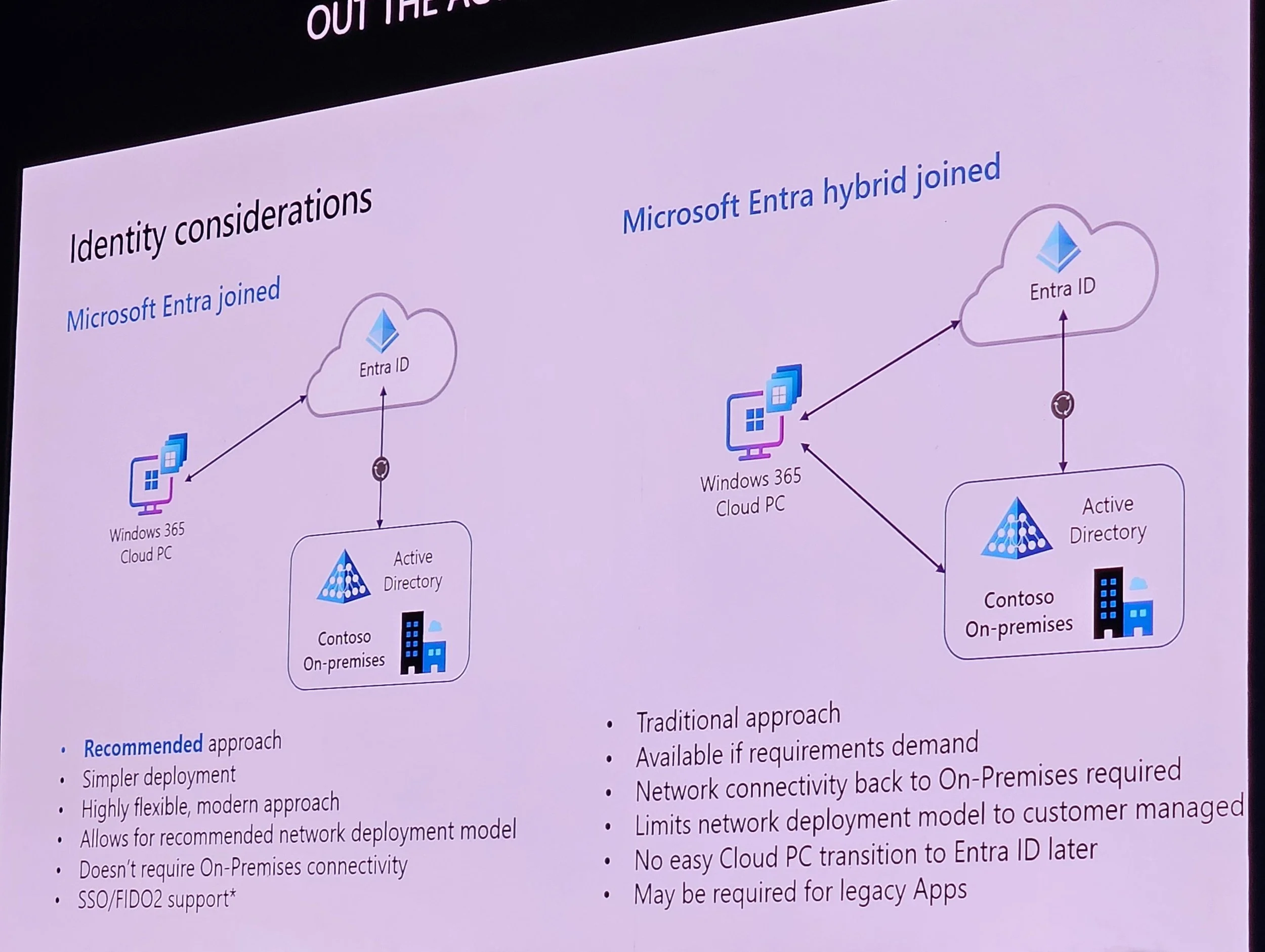
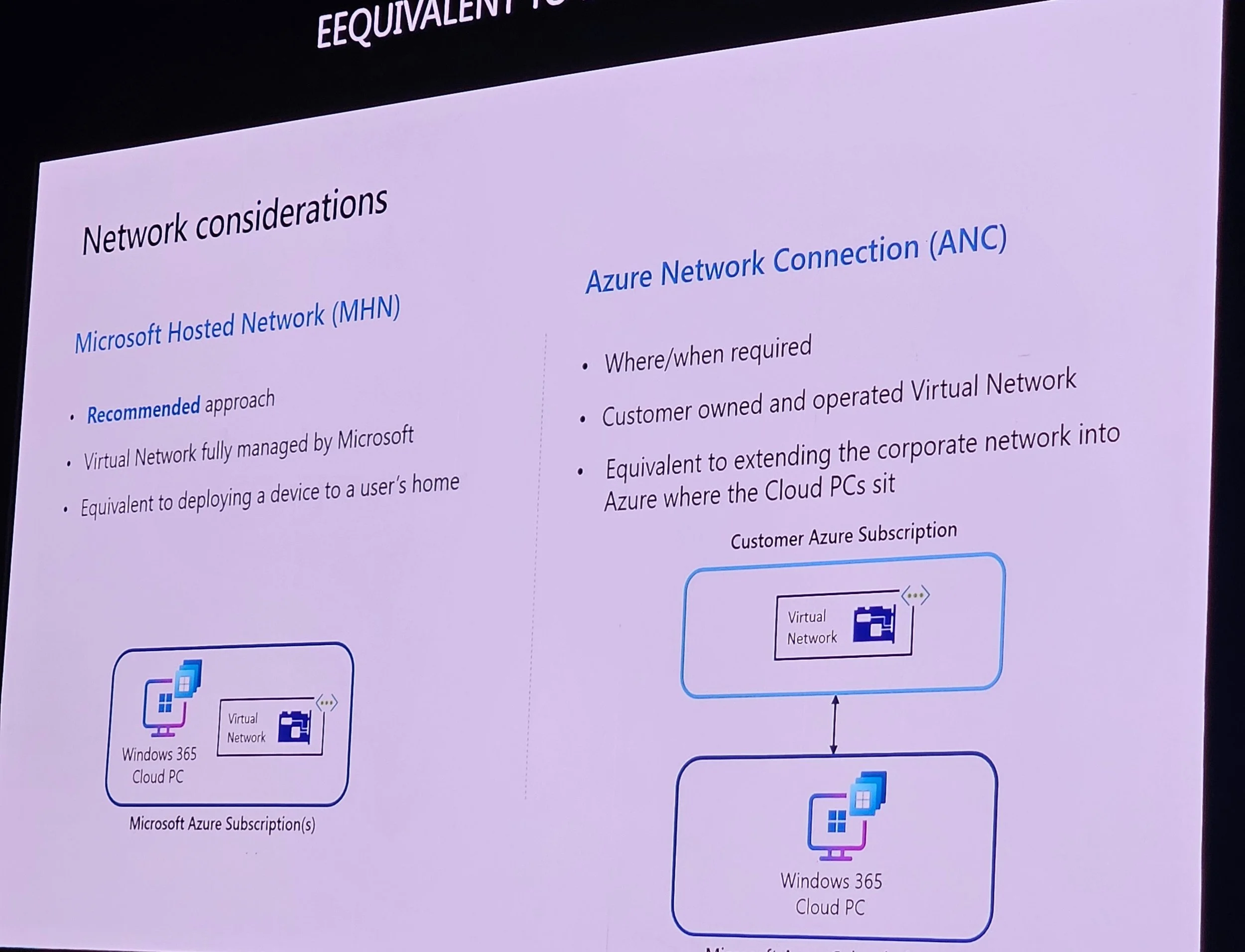
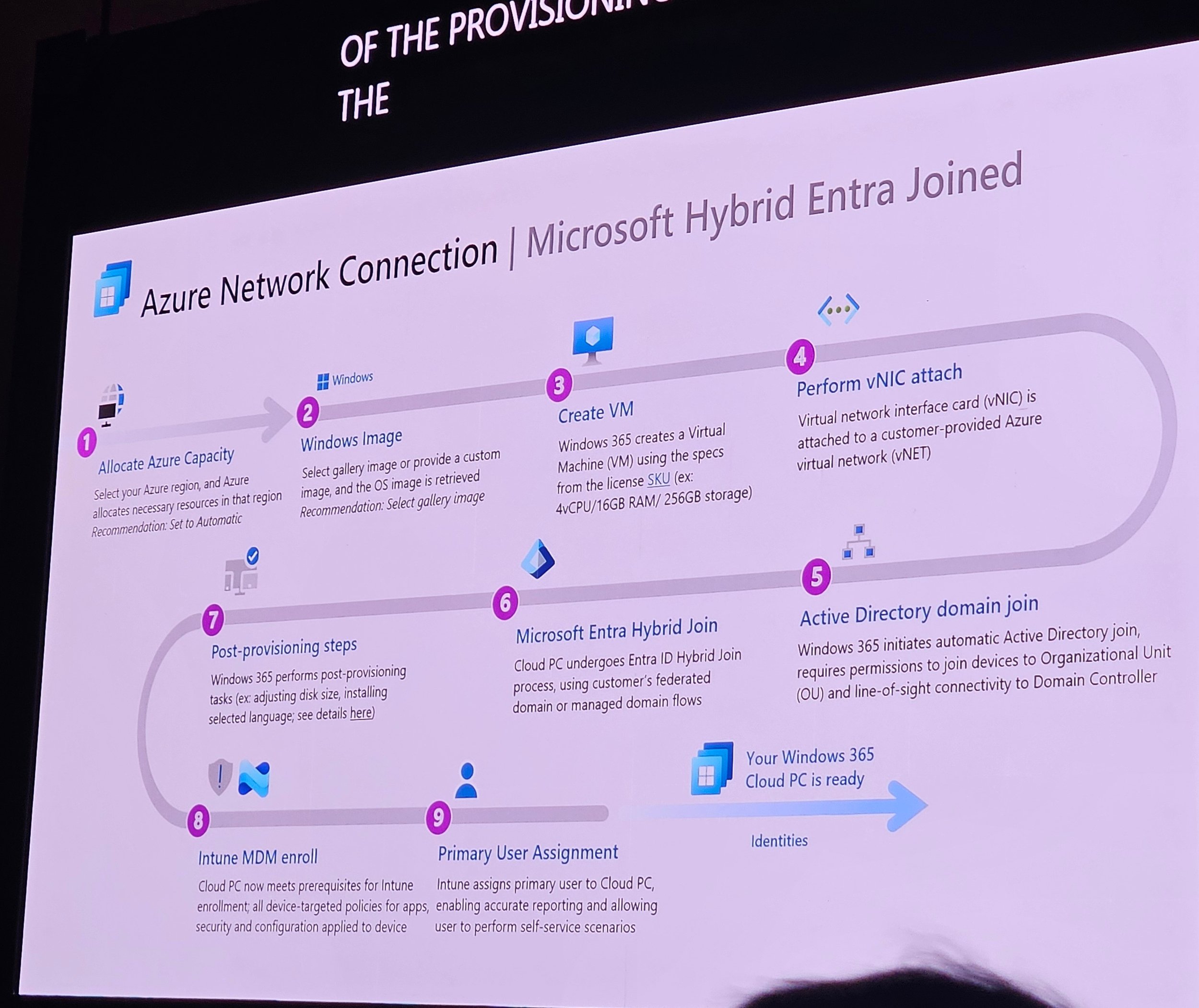
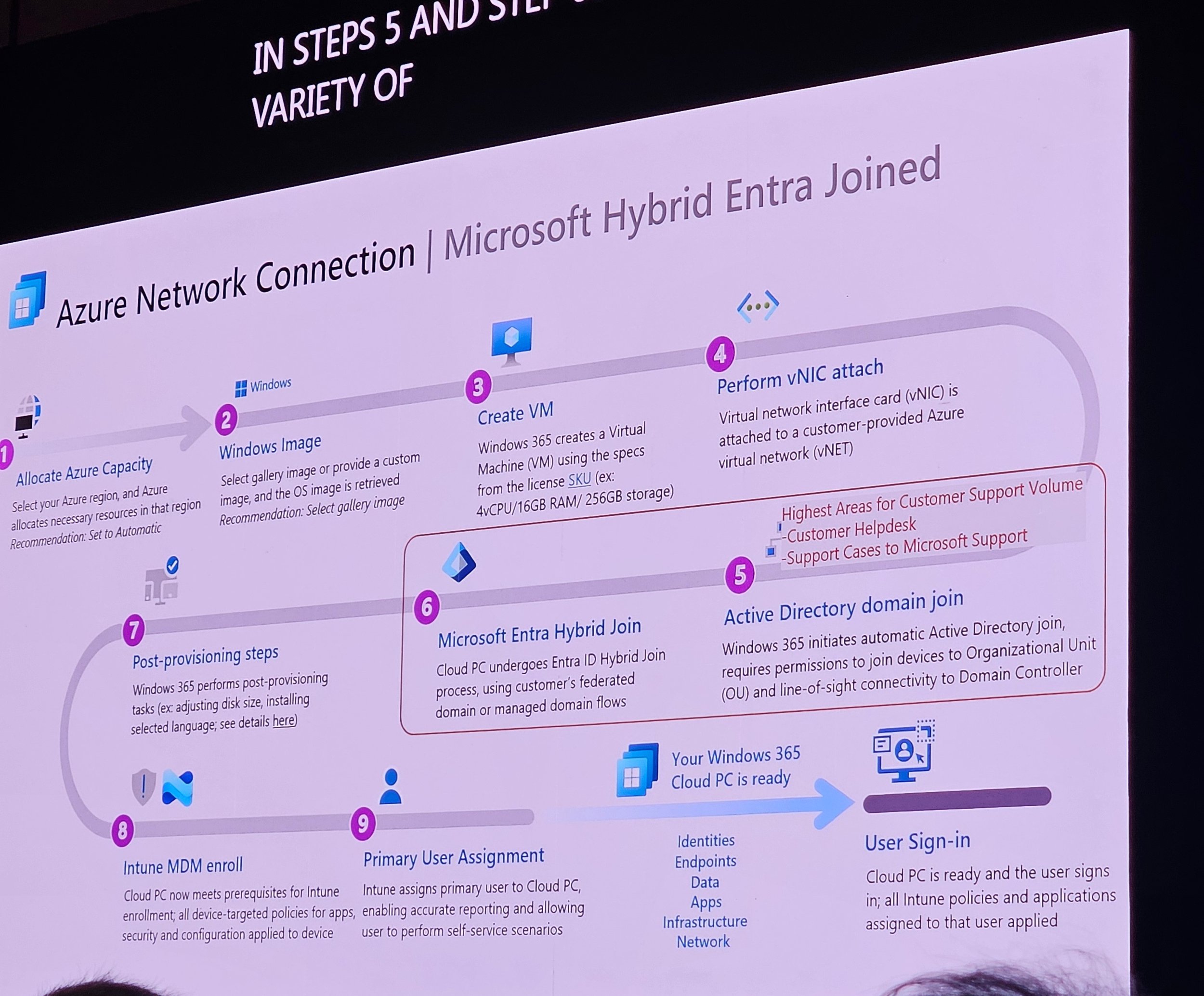
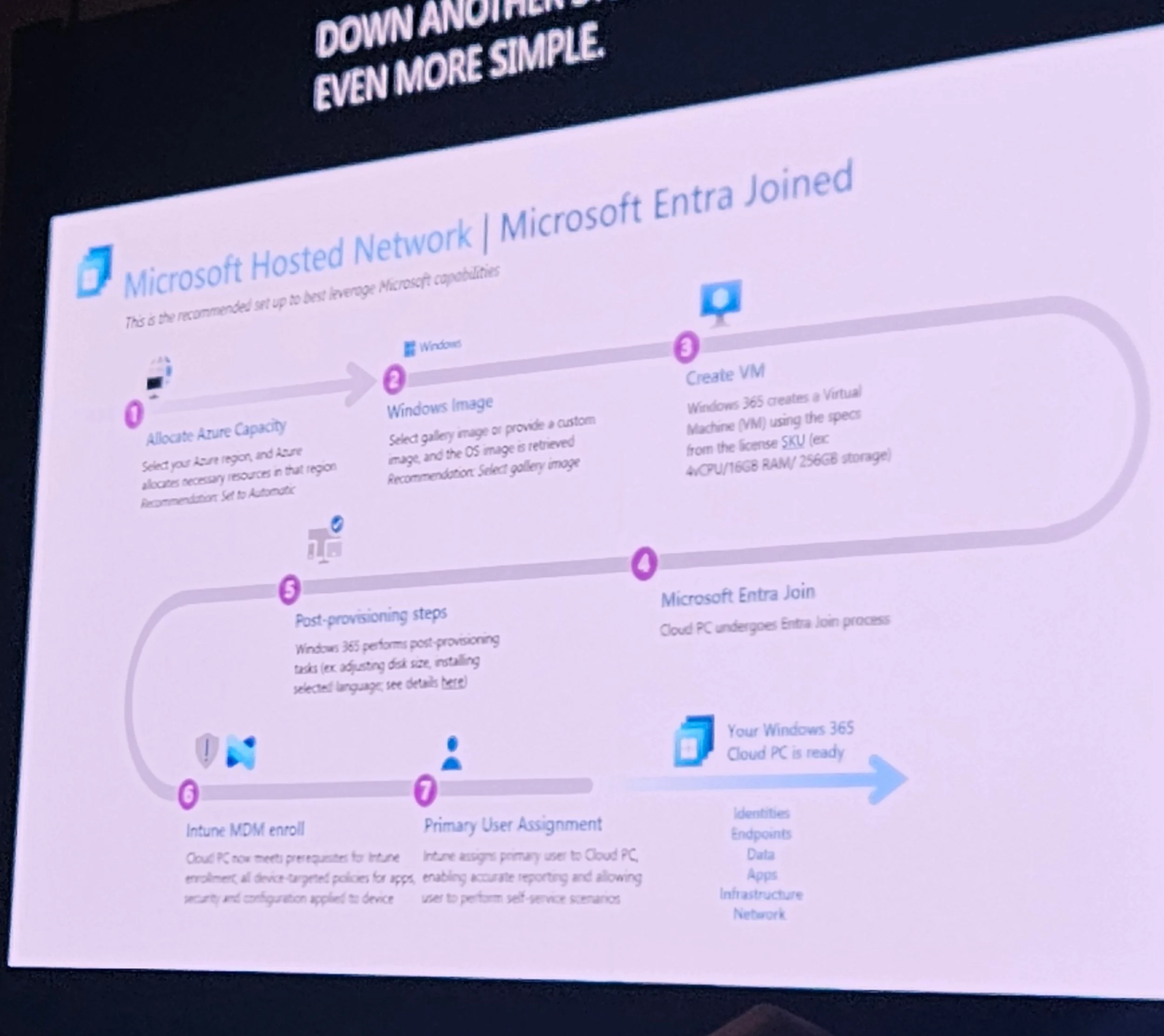
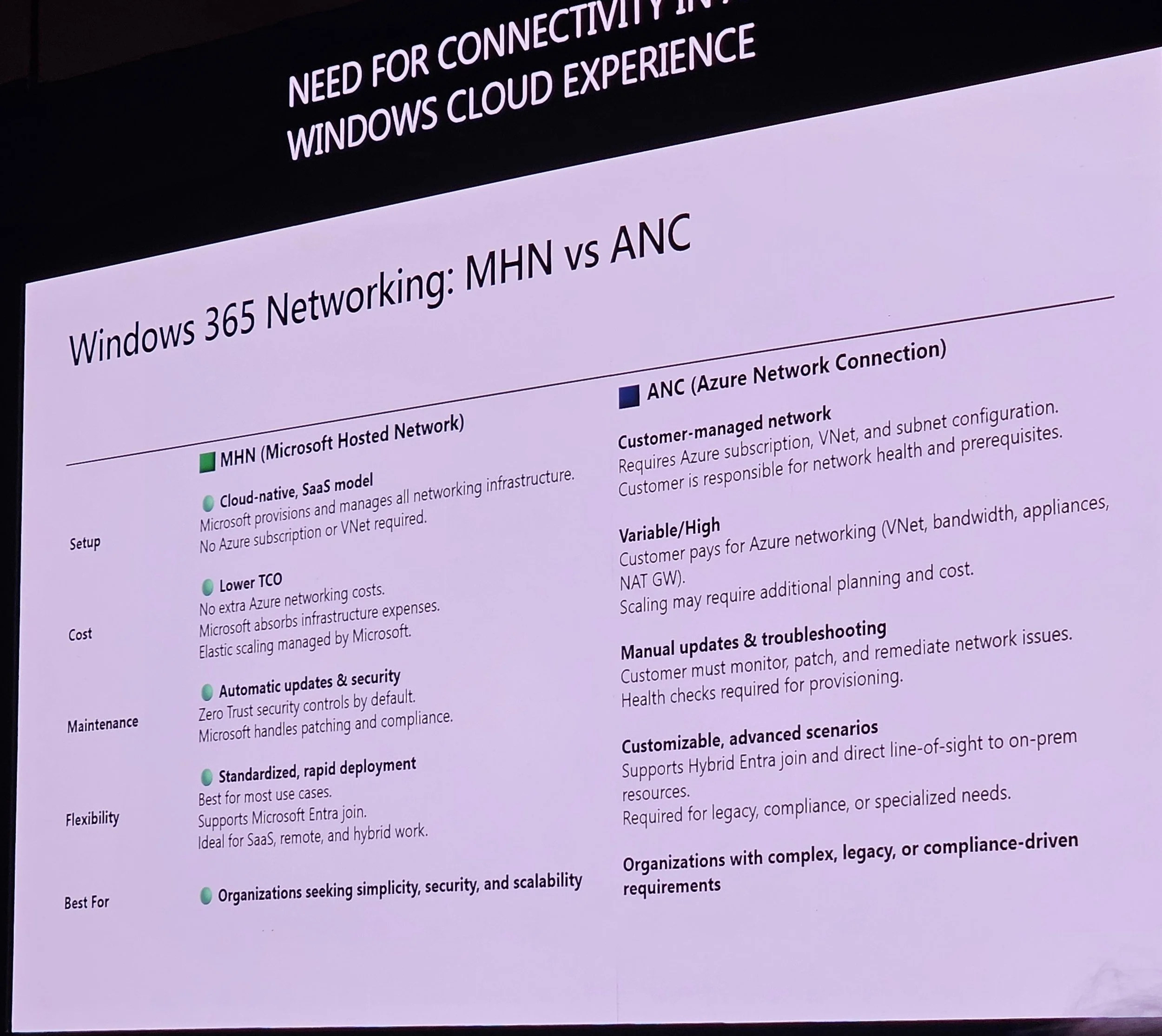
Hybrid Entra join is most problematic; Entra join with ANC is simpler.
Network: Microsoft Hosted Network (MHN) is simpler and cost-effective; Azure Network Connection (ANC) offers more control.
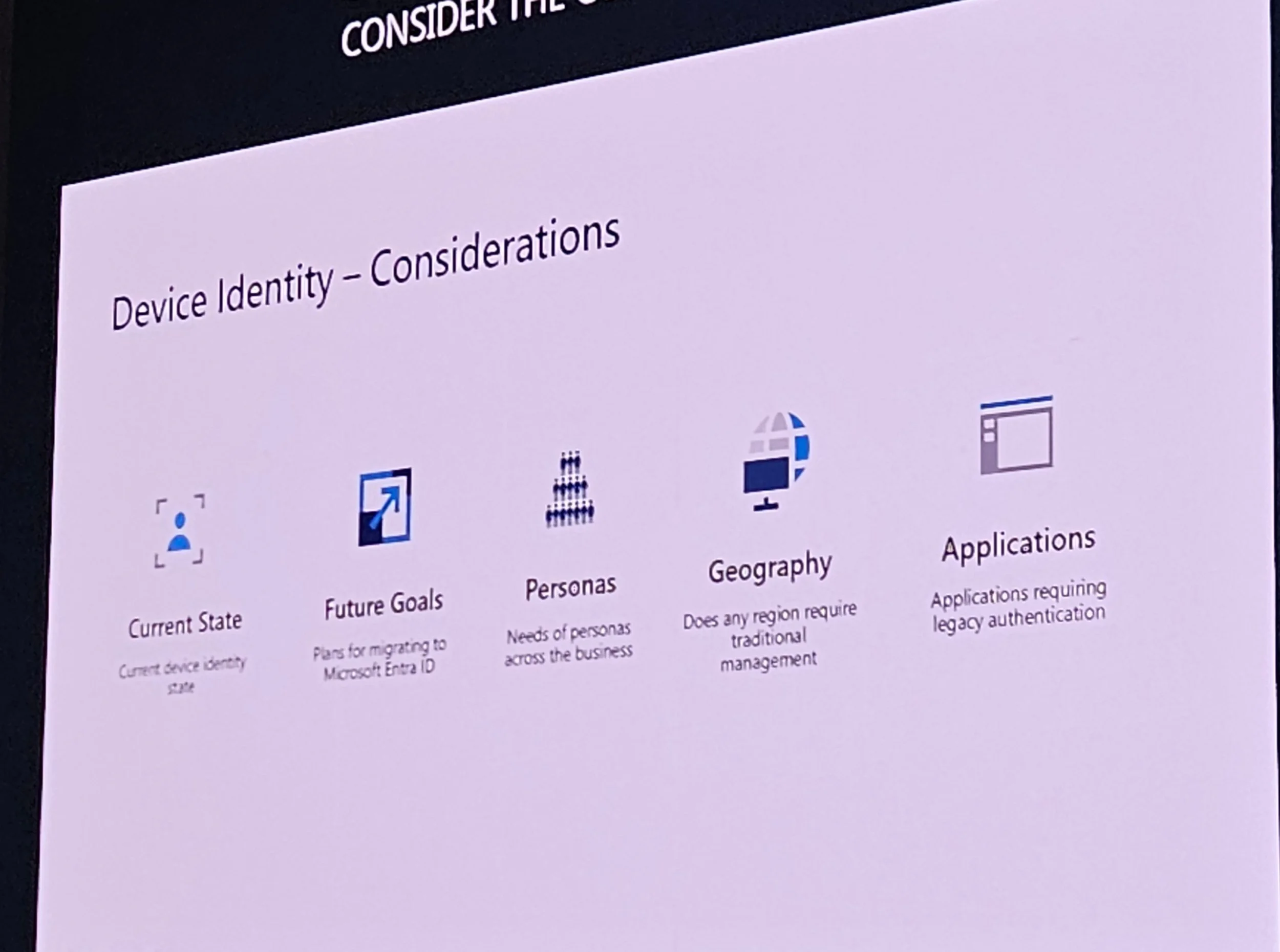
Considerations: Identity, on-prem needs, simplicity, cost, flexibility.
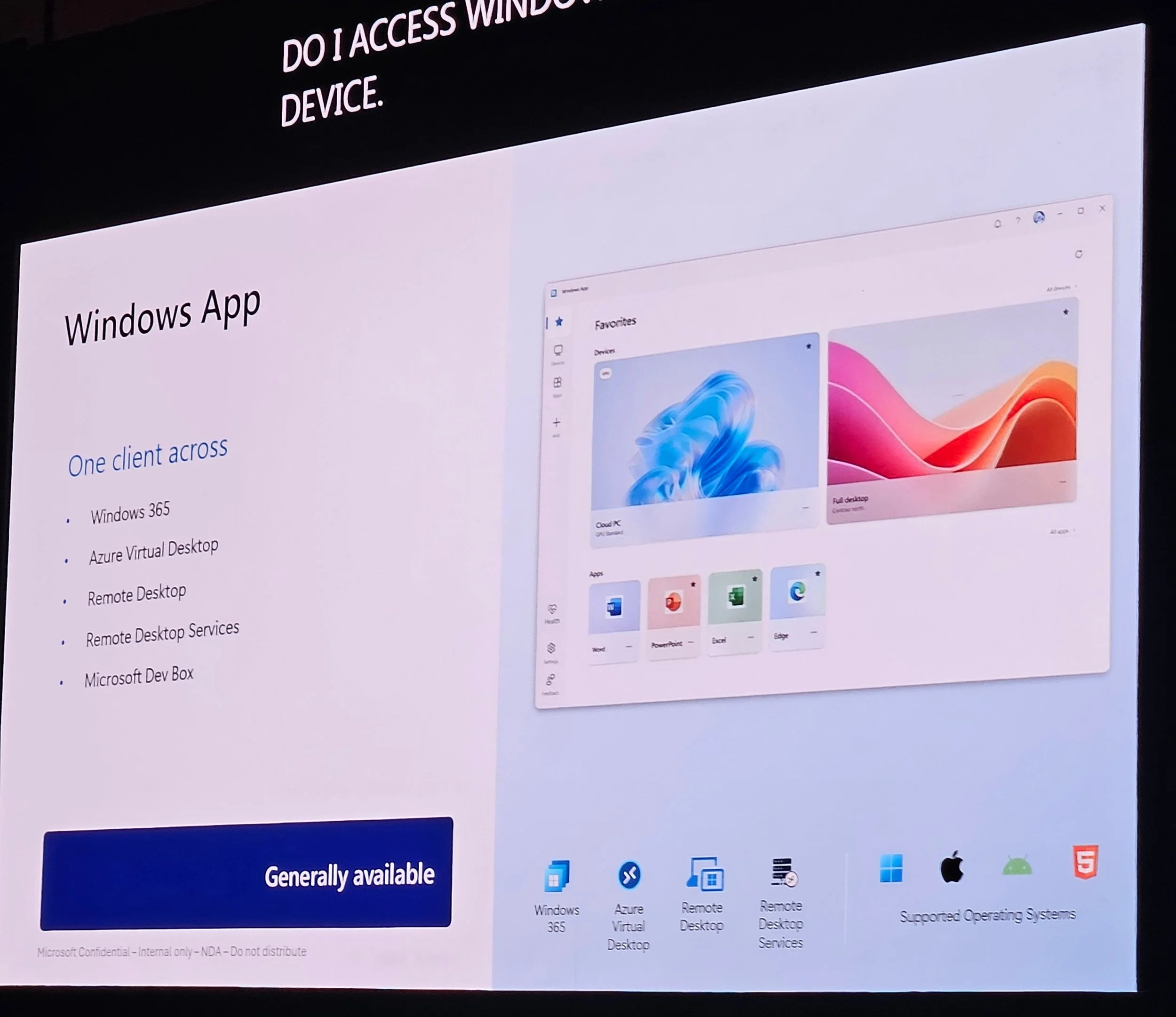
4. End User Experience & The Windows App
Linda Zhu covered the Windows app:
One client for Windows 365, AVD, Remote Desktop, Dev Box.
Available on all major platforms; MSI installers for Windows/Mac.
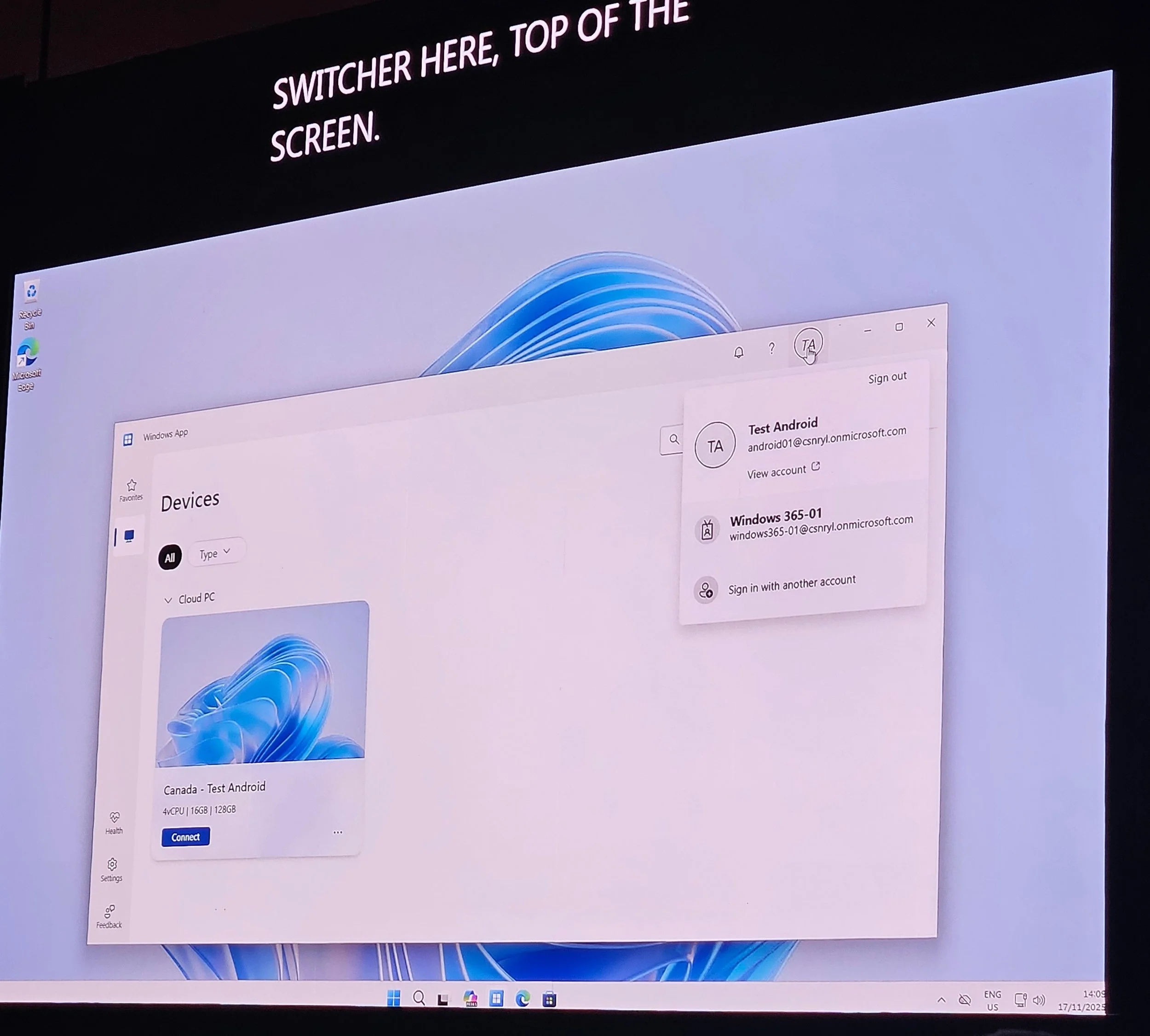
Features: Identity switcher, device favorites, right-click options (restart, rename, details), feedback hub.
Enhanced Teams experiences.
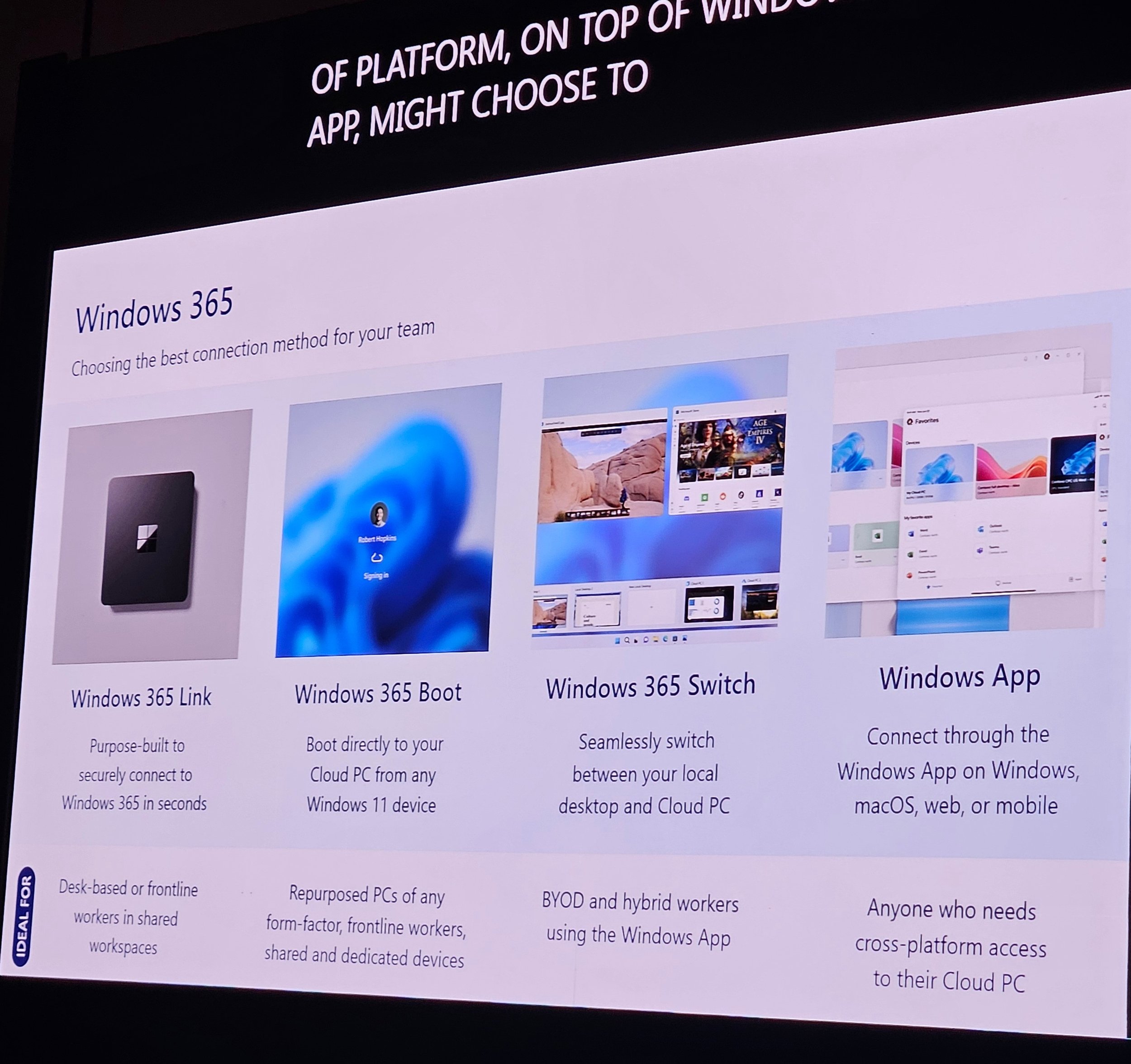
W365 Boot: Boot Win11 devices directly to Cloud PC.
W365 Switch: Toggle between local and Cloud PC.
W365 Link: Access Cloud PC only; limited peripheral support (for now).
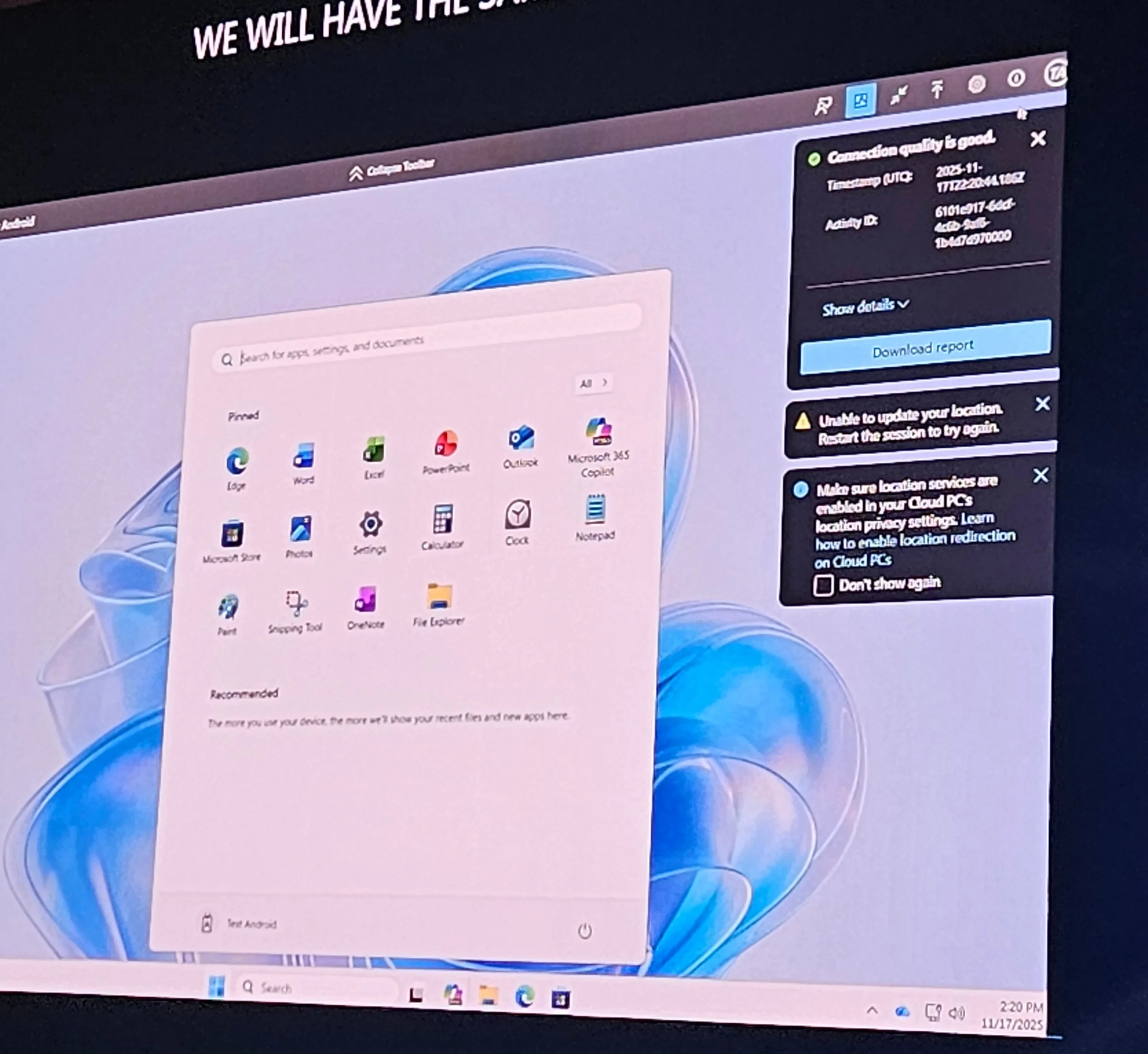
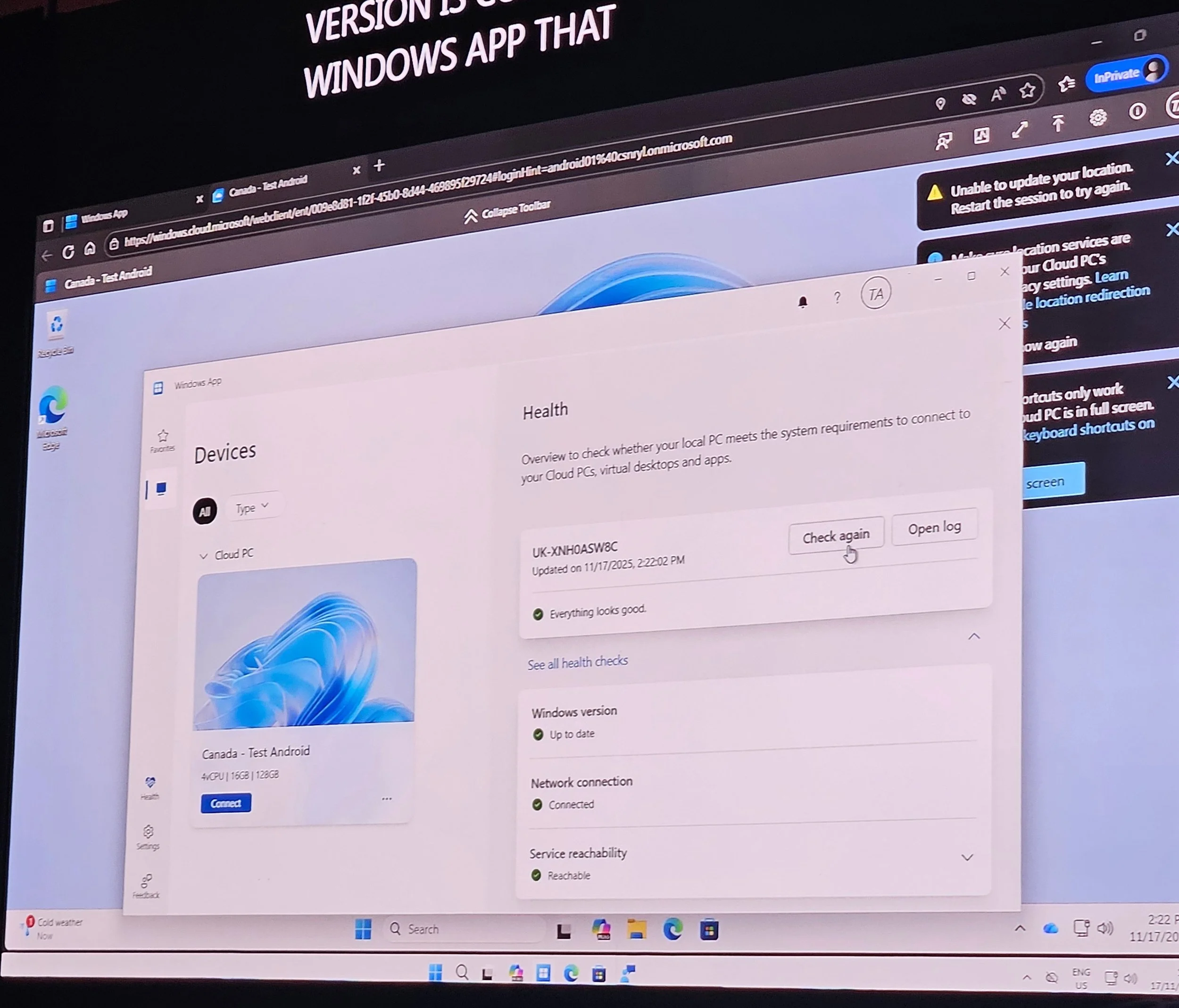
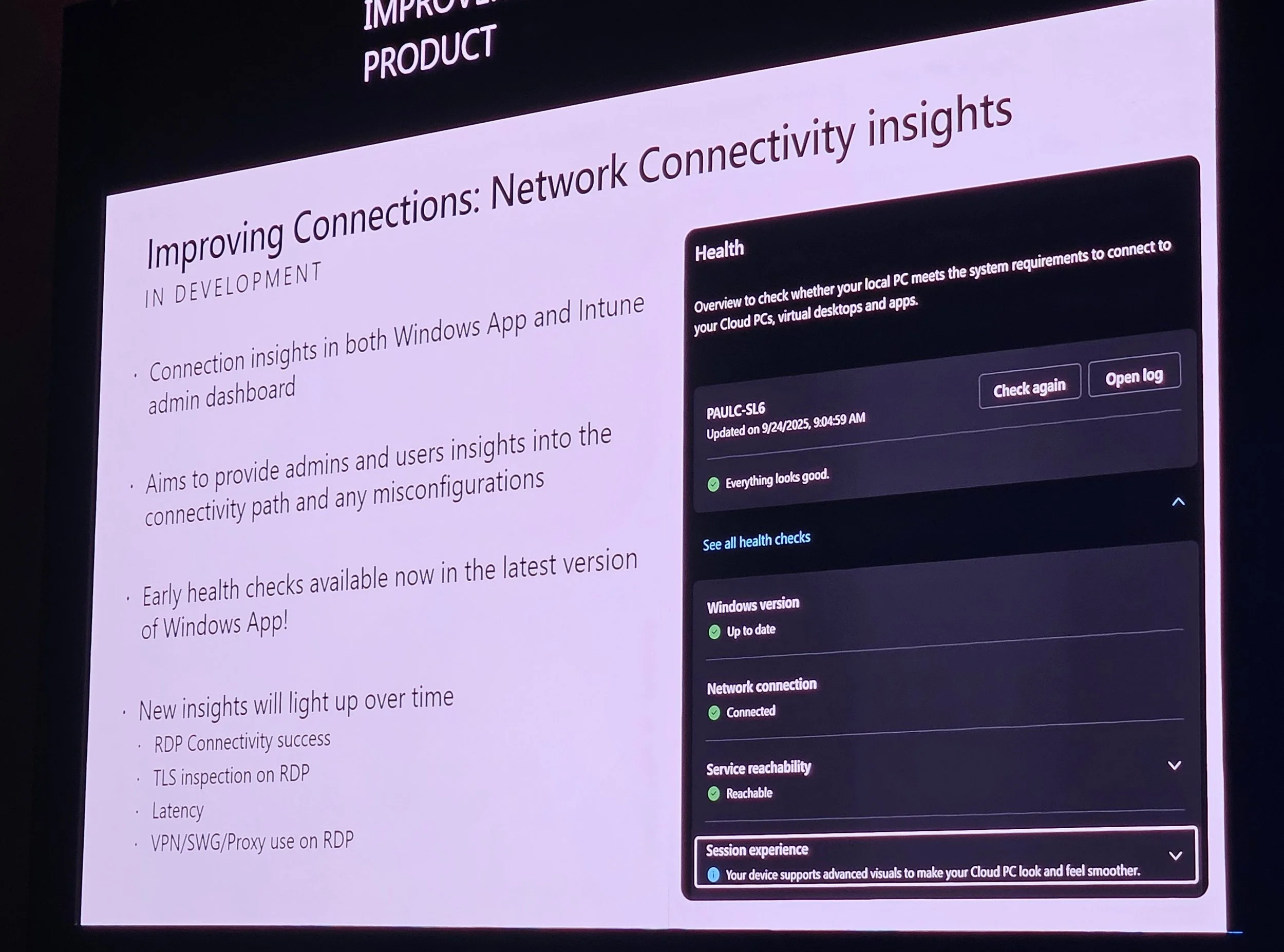
Troubleshooting tools: Connection inspection, health checks, diagnostics sent to Intune.
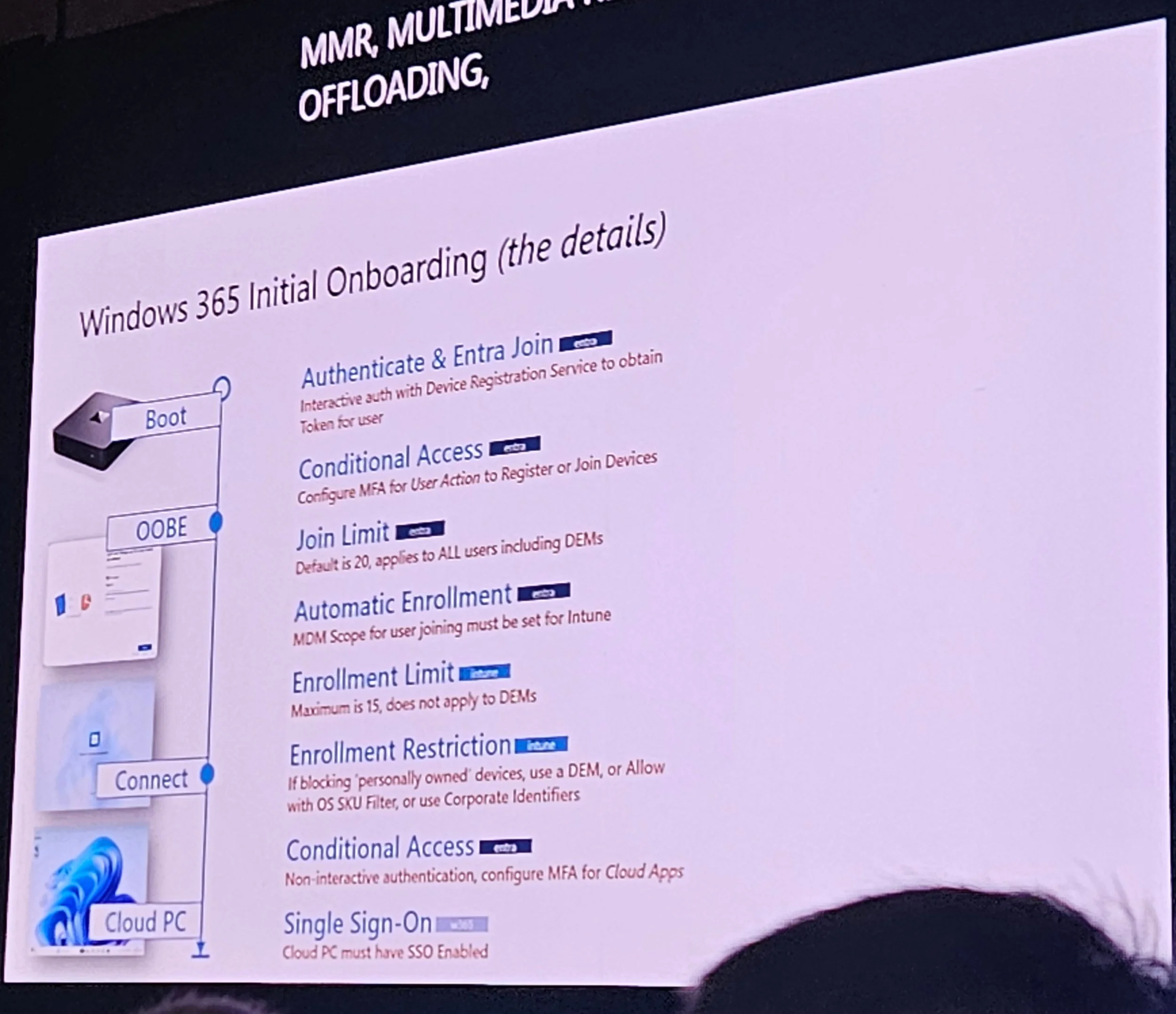
5. Connectivity & Network Optimization
Angelo discussed MHN vs ANC (see screenshots for details).
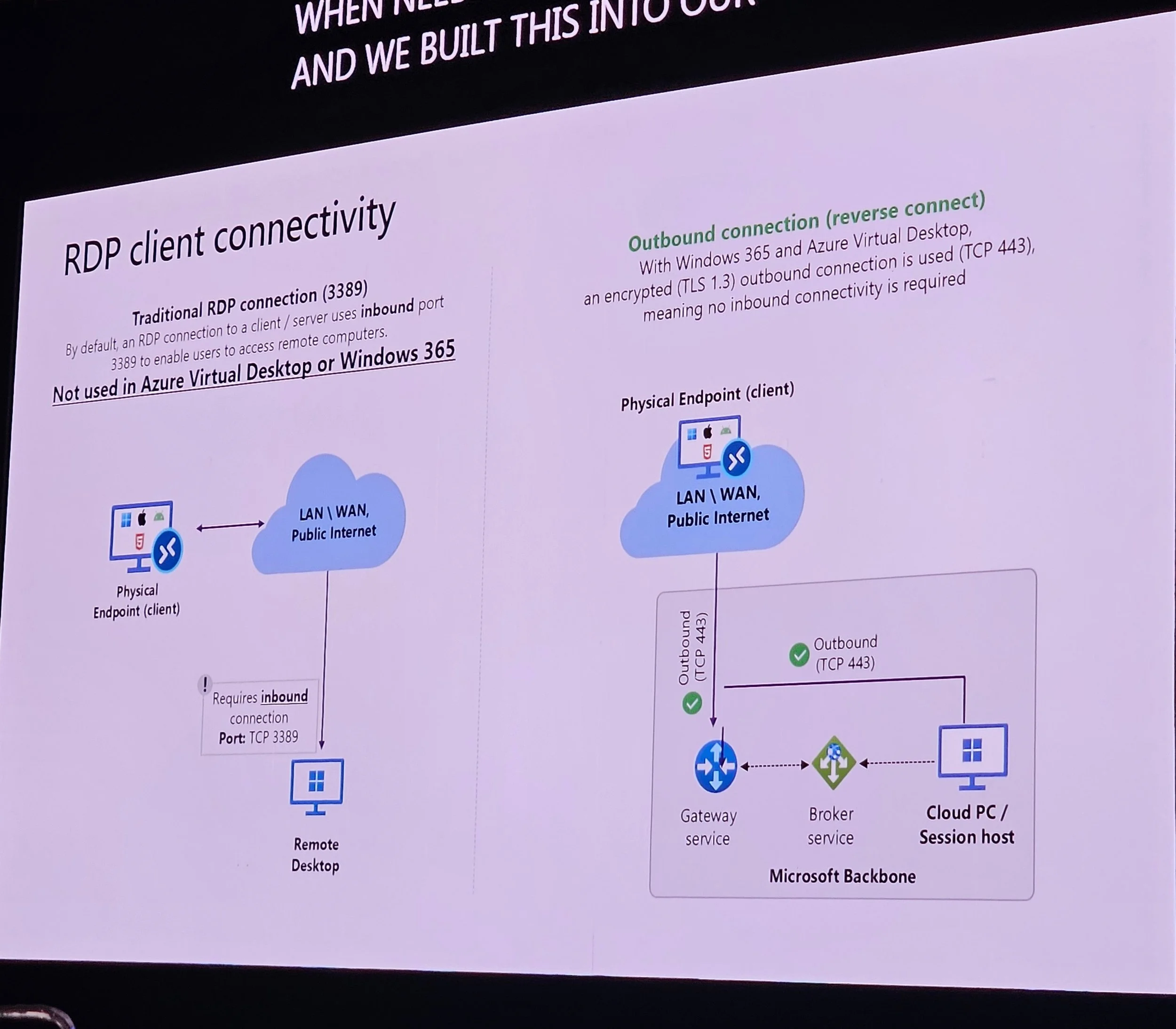
W365 uses outbound TCP 443 (reverse connect), TLS 1.3 encrypted.
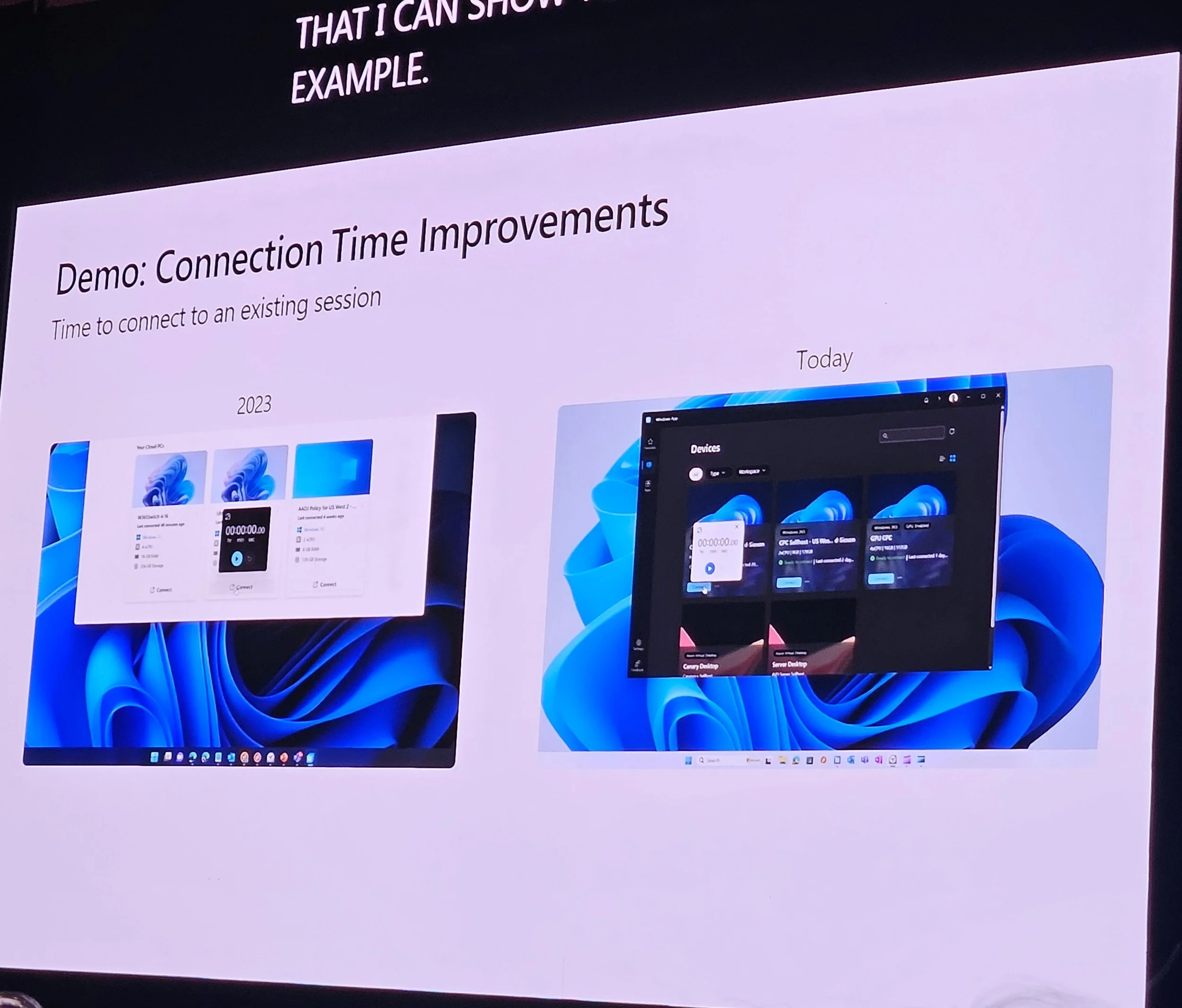
Connection speed improved: 23s (2023) → 7s (now).
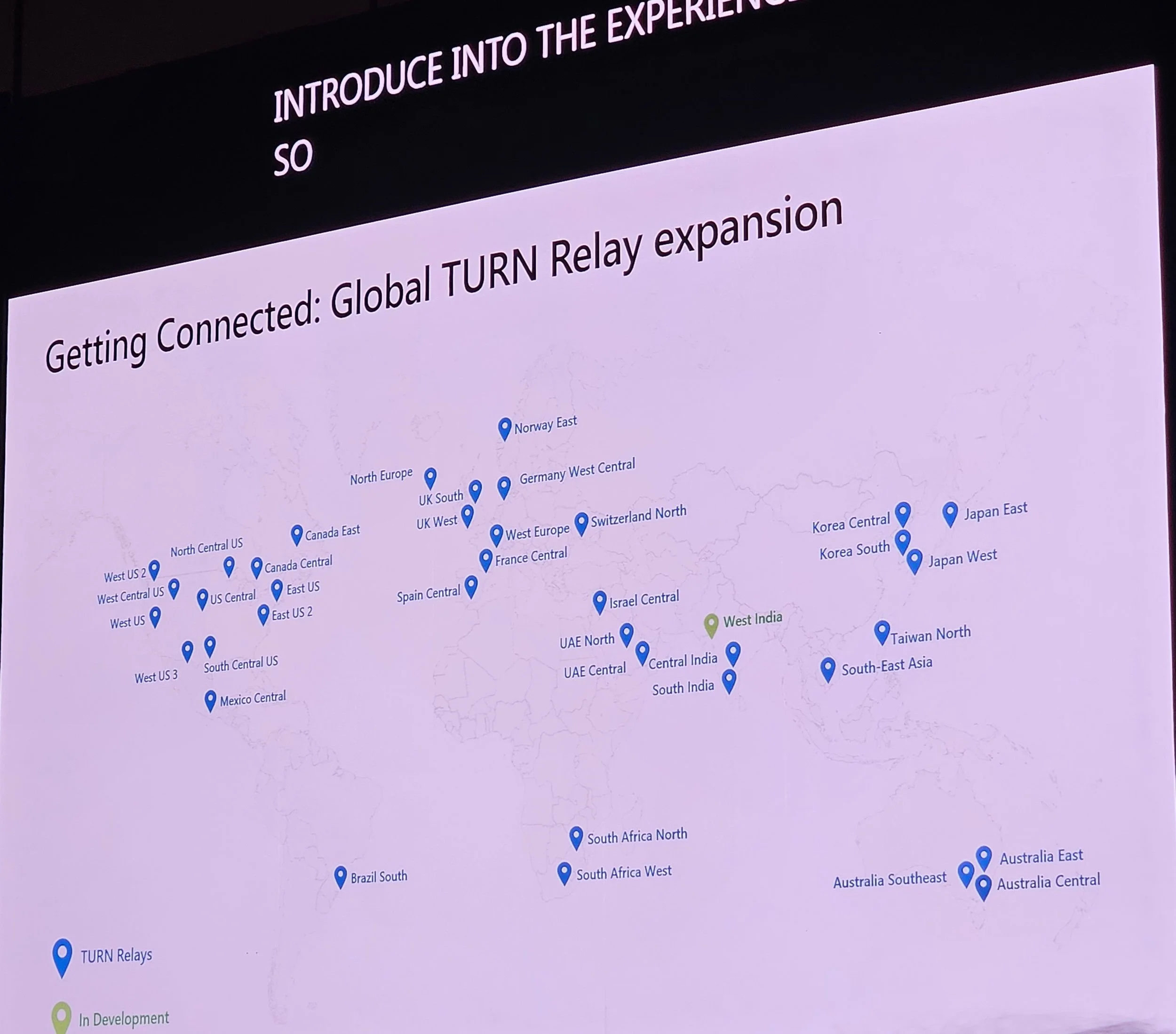
UDP/Global TURN Relay expansion for better RDP performance.
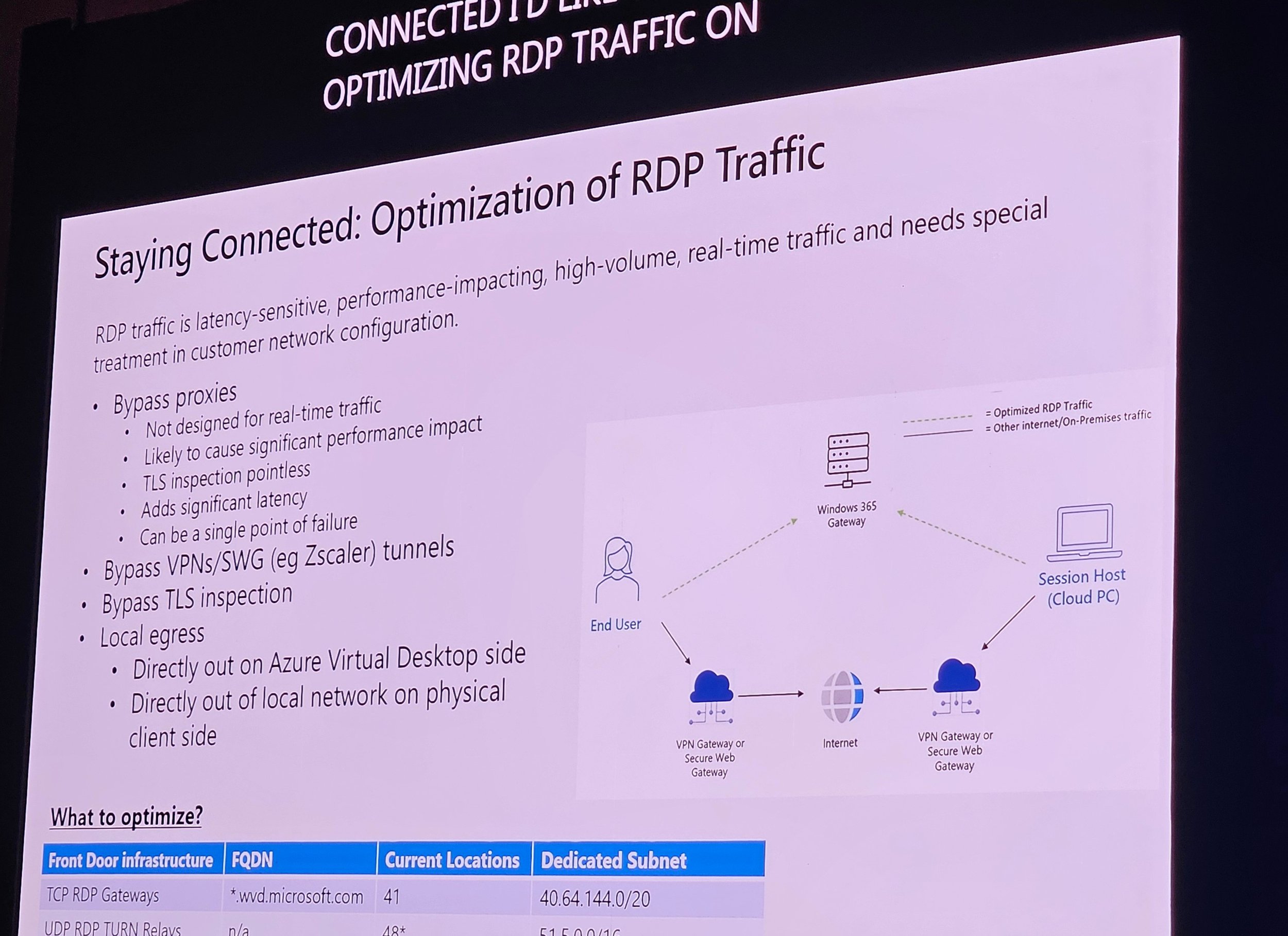
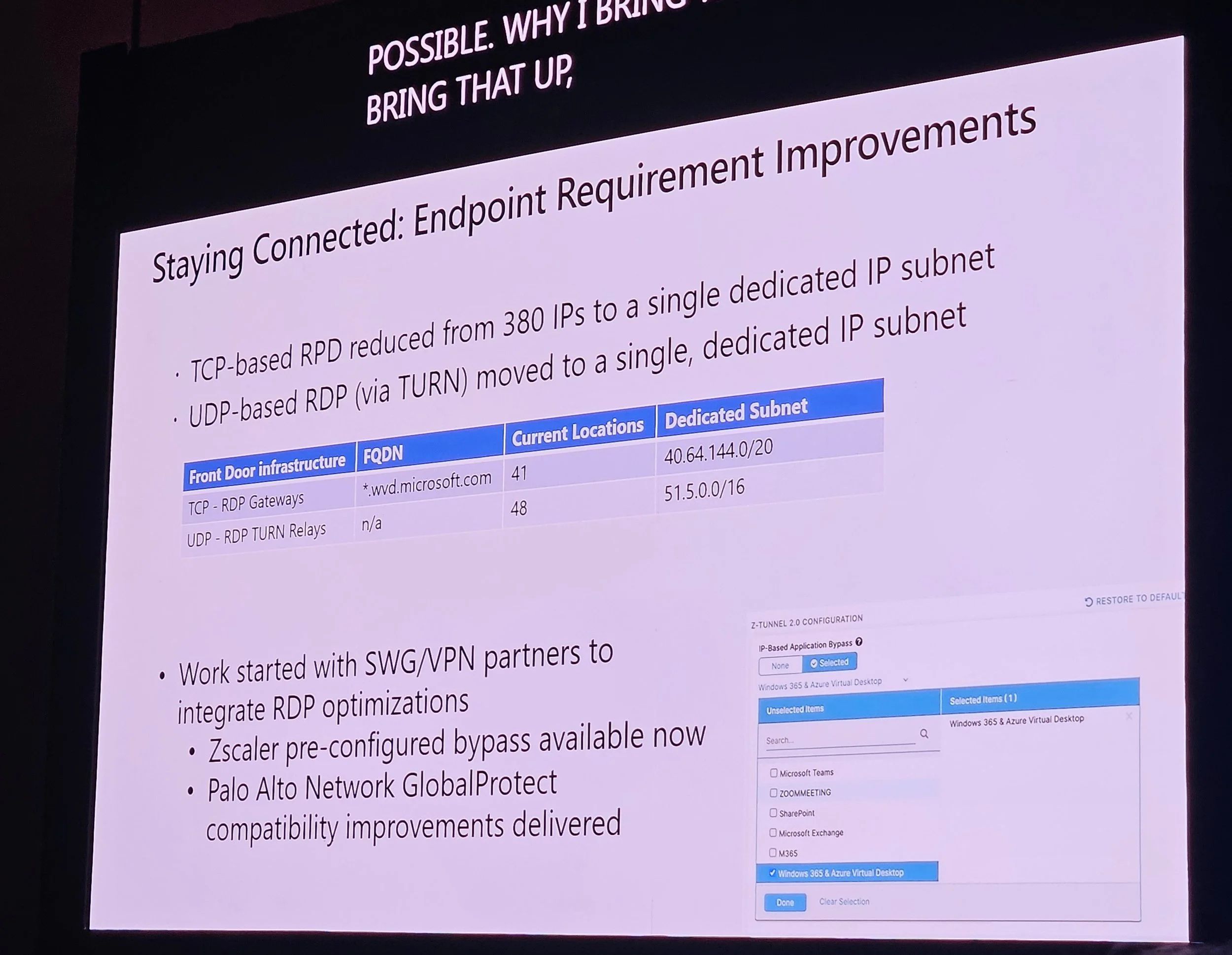
Dedicated IP ranges for W365/AVD traffic.
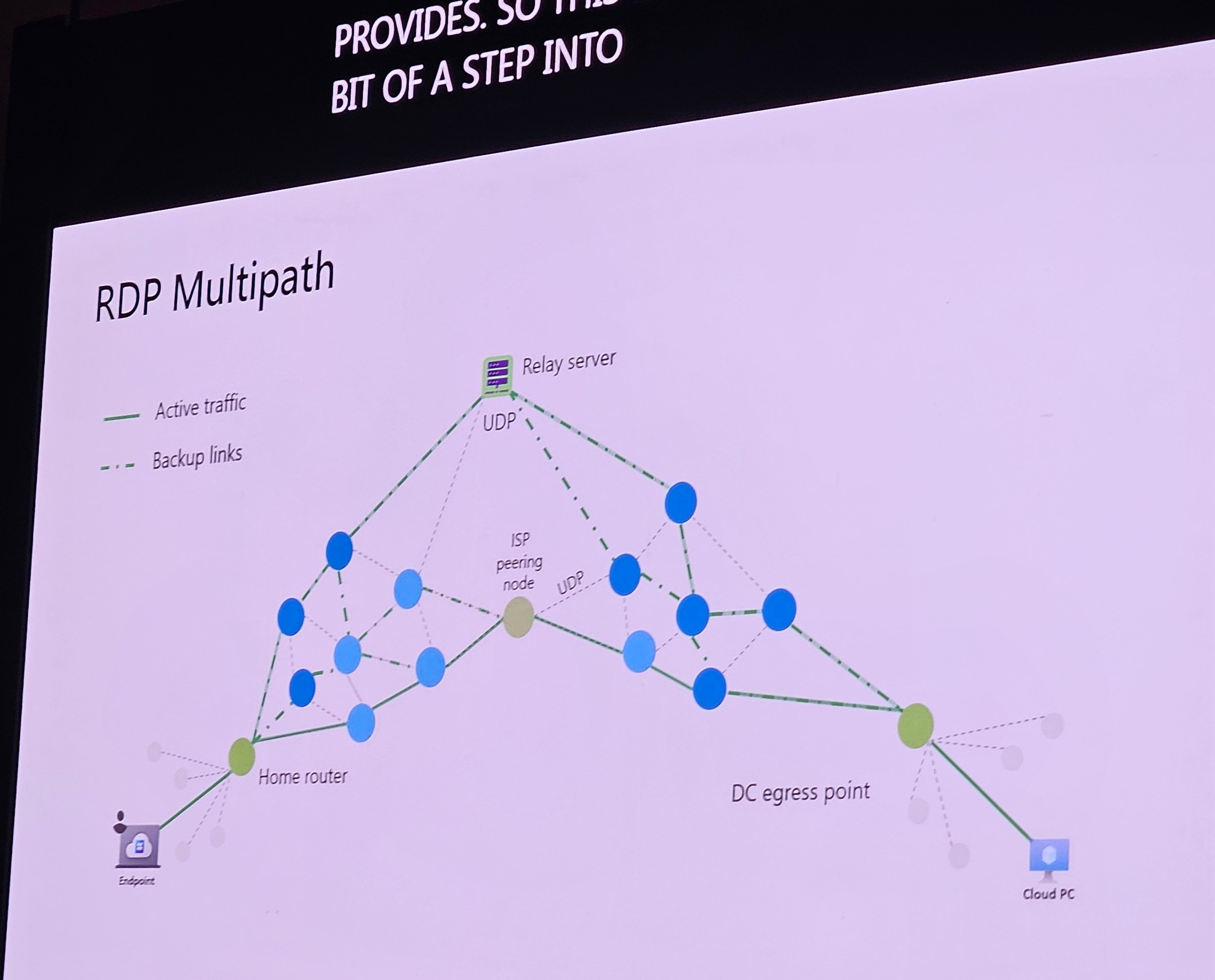
RDP multipath with UDP: Automatic failover, no user/admin action needed.
Proxy bypass for RDP traffic recommended.
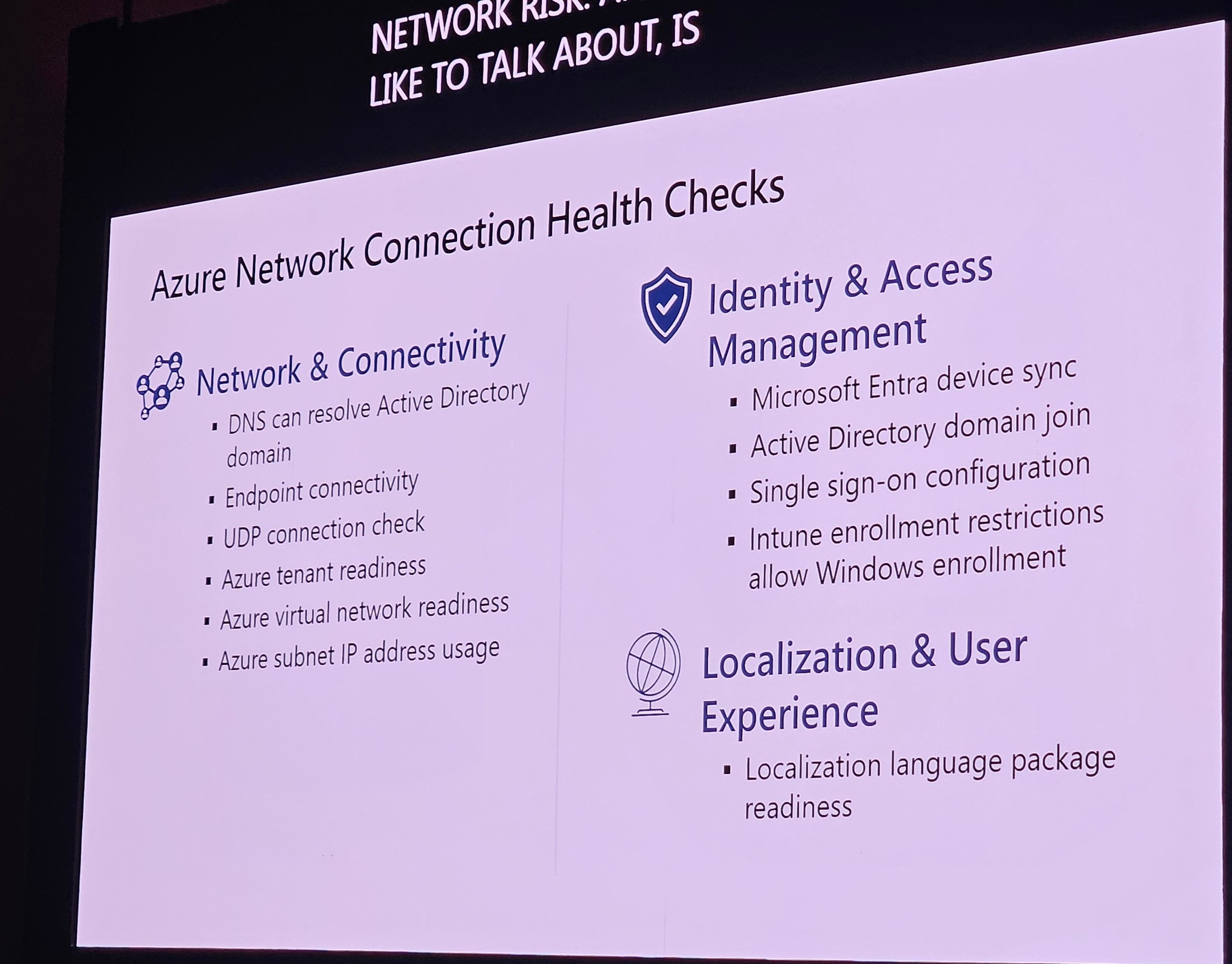
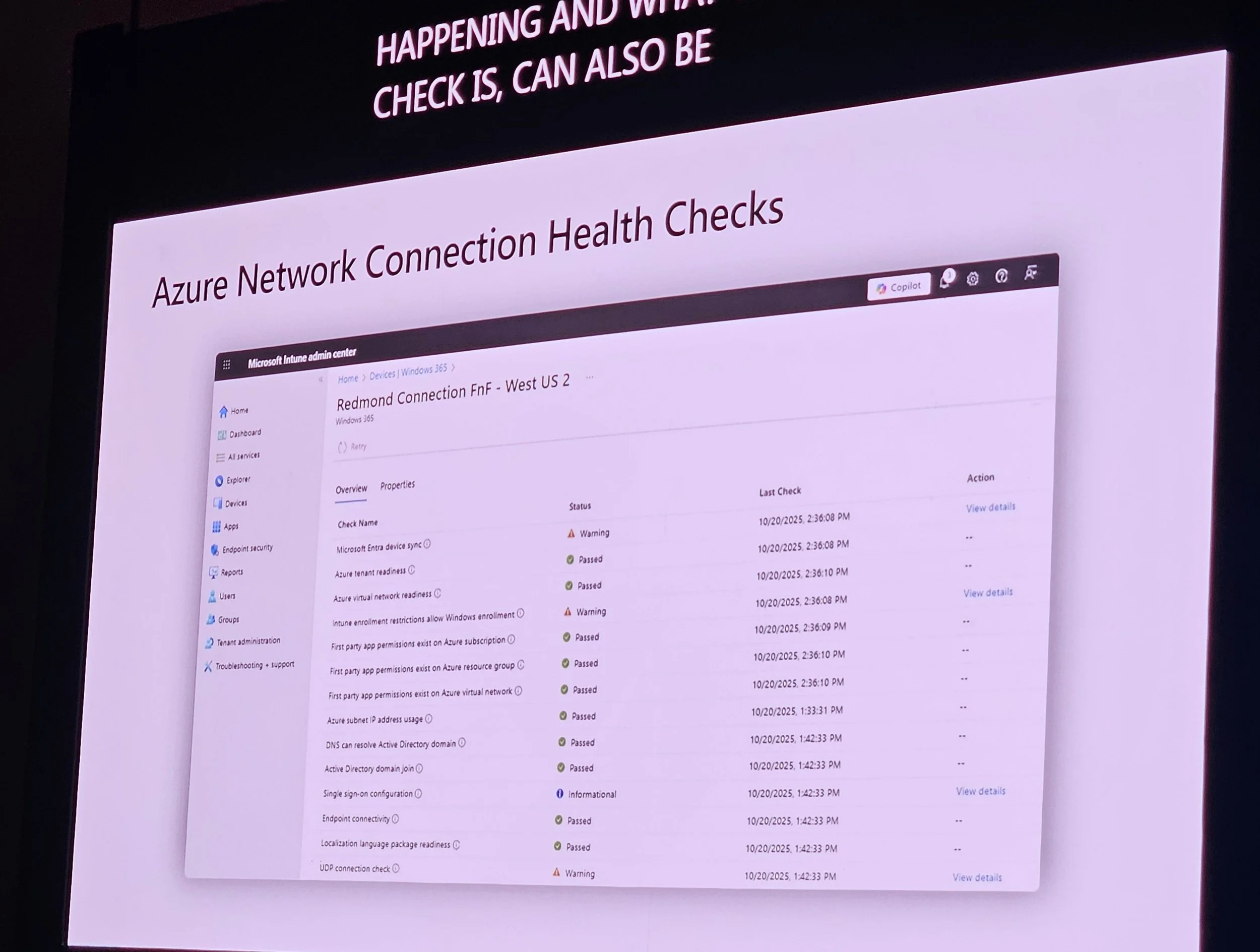
Health checks in Intune admin center; failed checks block provisioning.
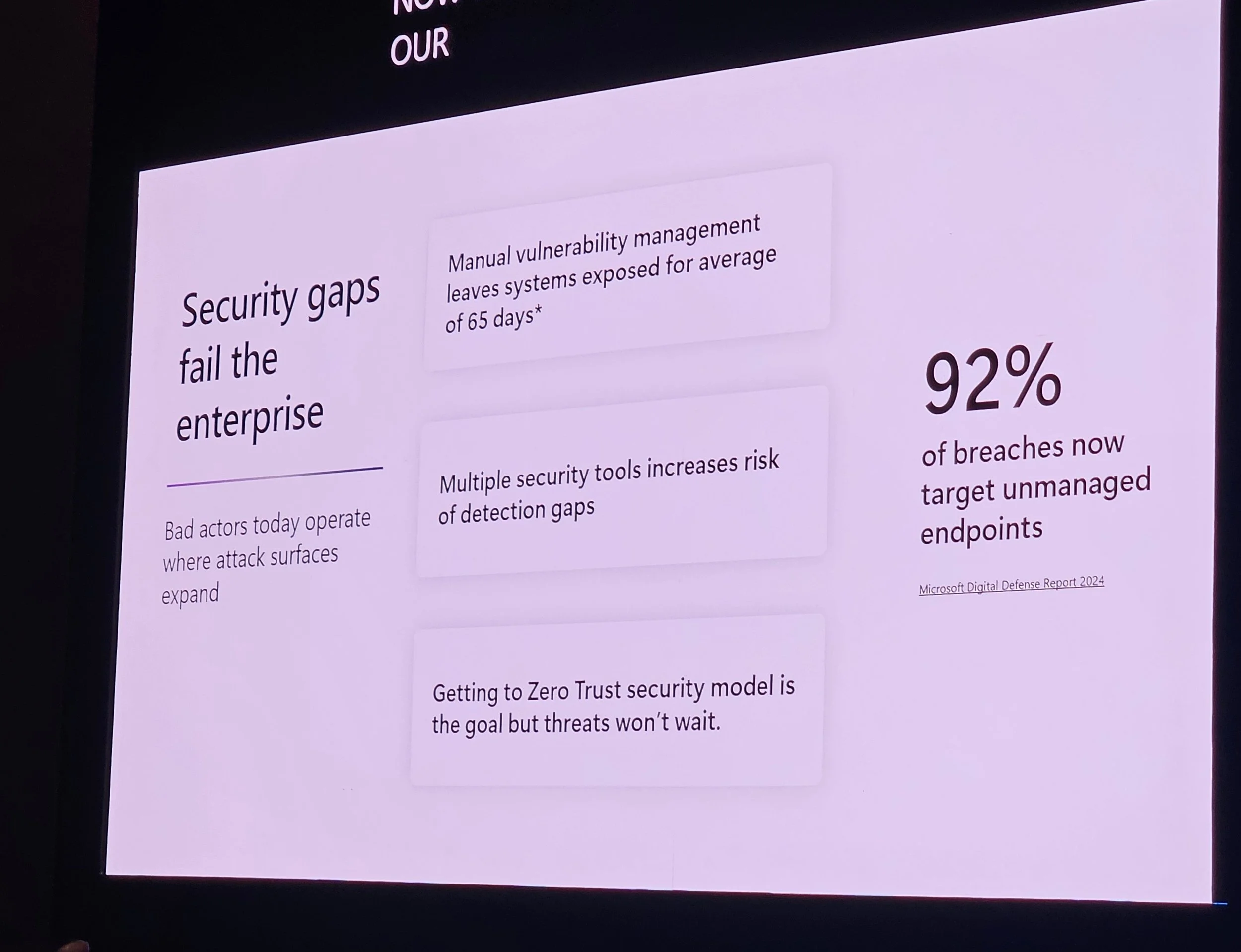
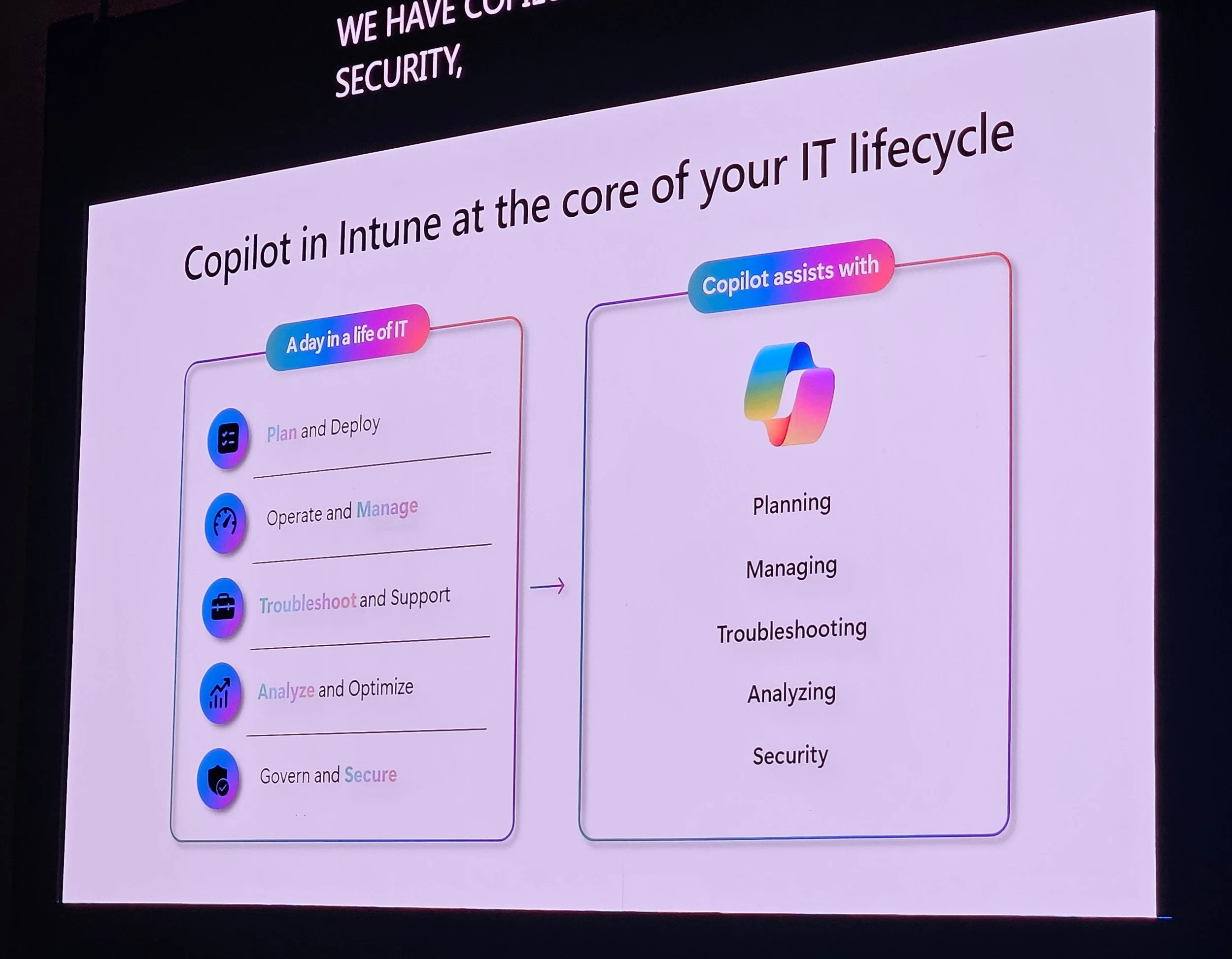
6. Intune Suite & Security Copilot
Jon Callahan on Intune and Security Copilot:
Intune as Zero Trust foundation.
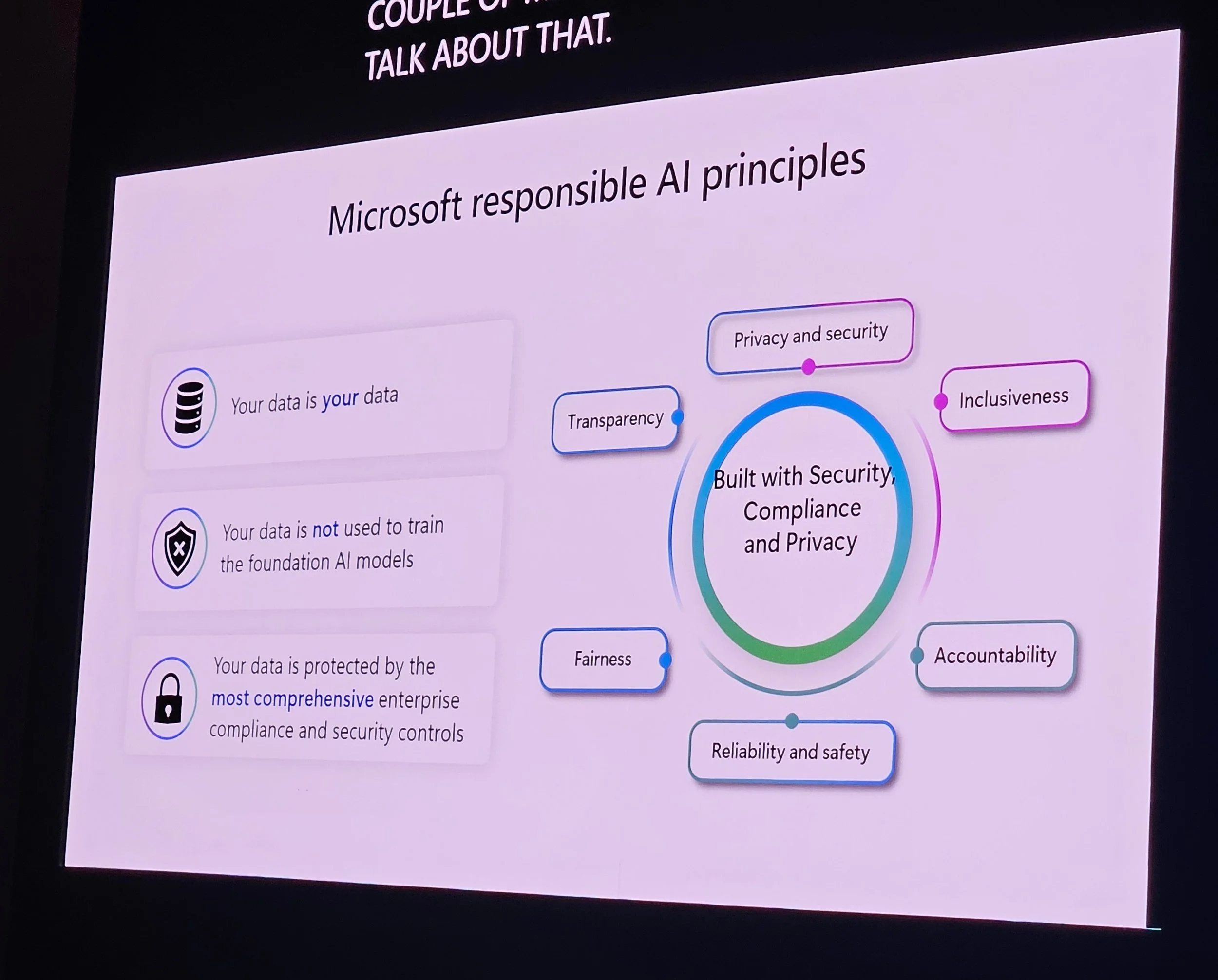
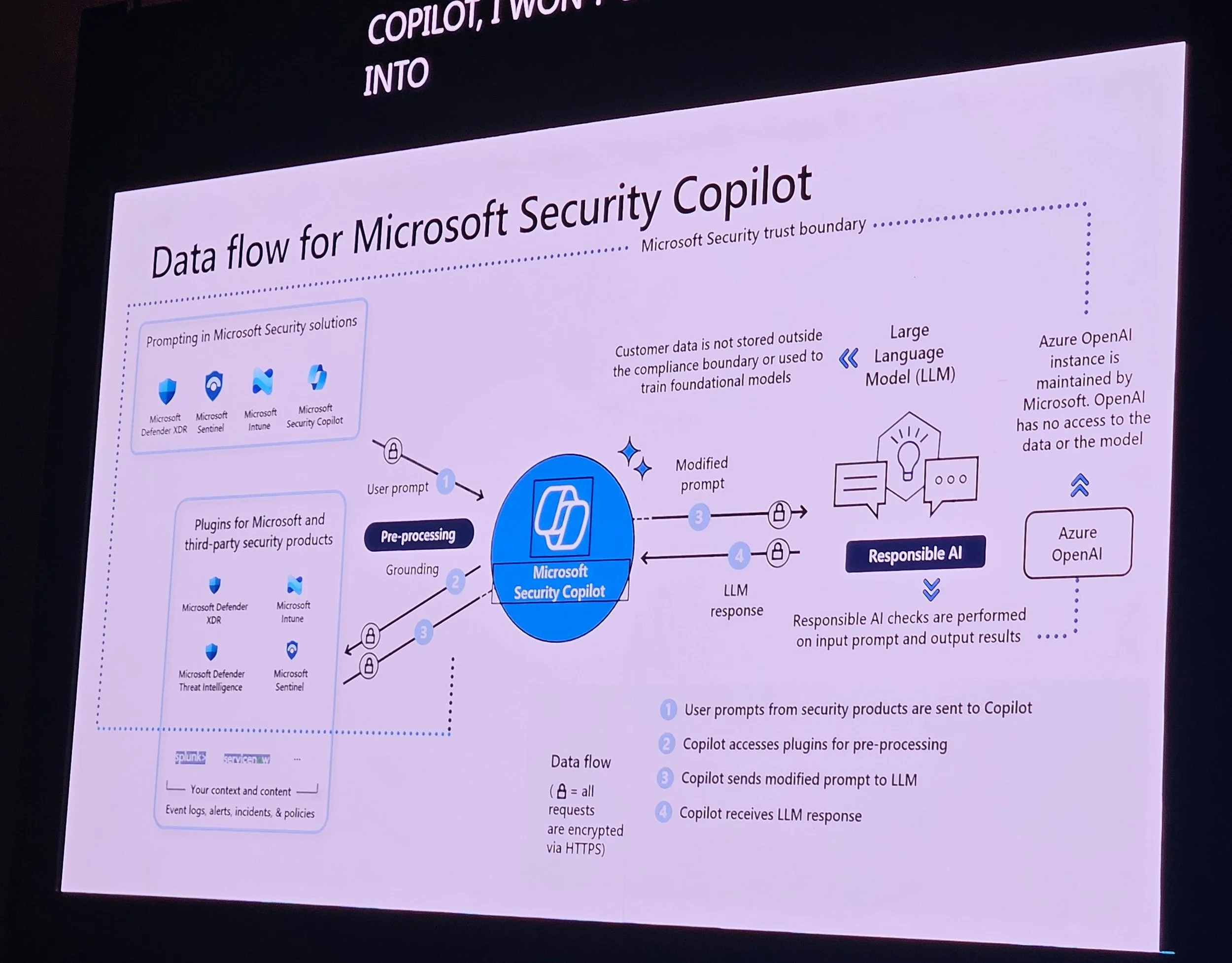
Copilot uses private Azure OpenAI; respects RBAC.
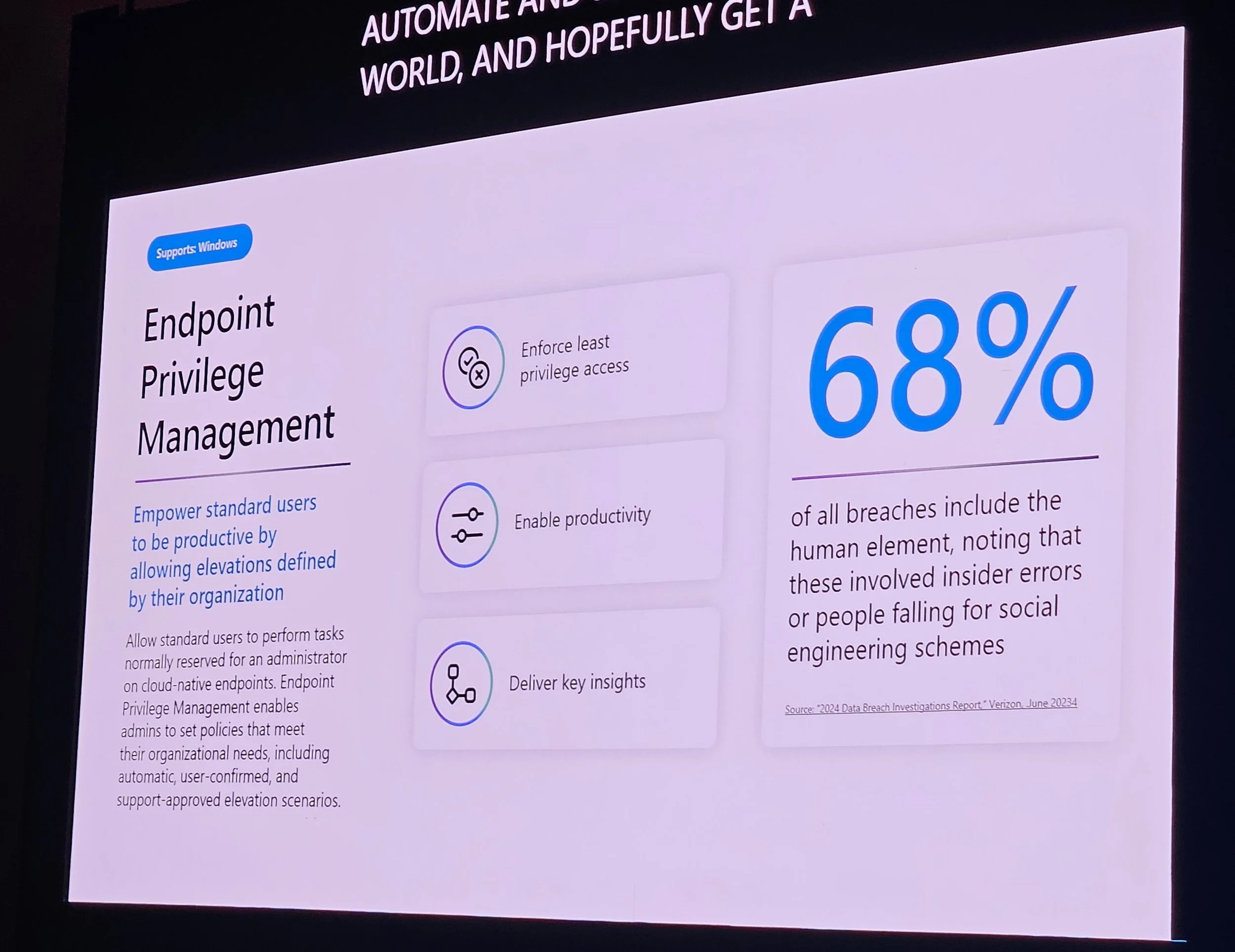
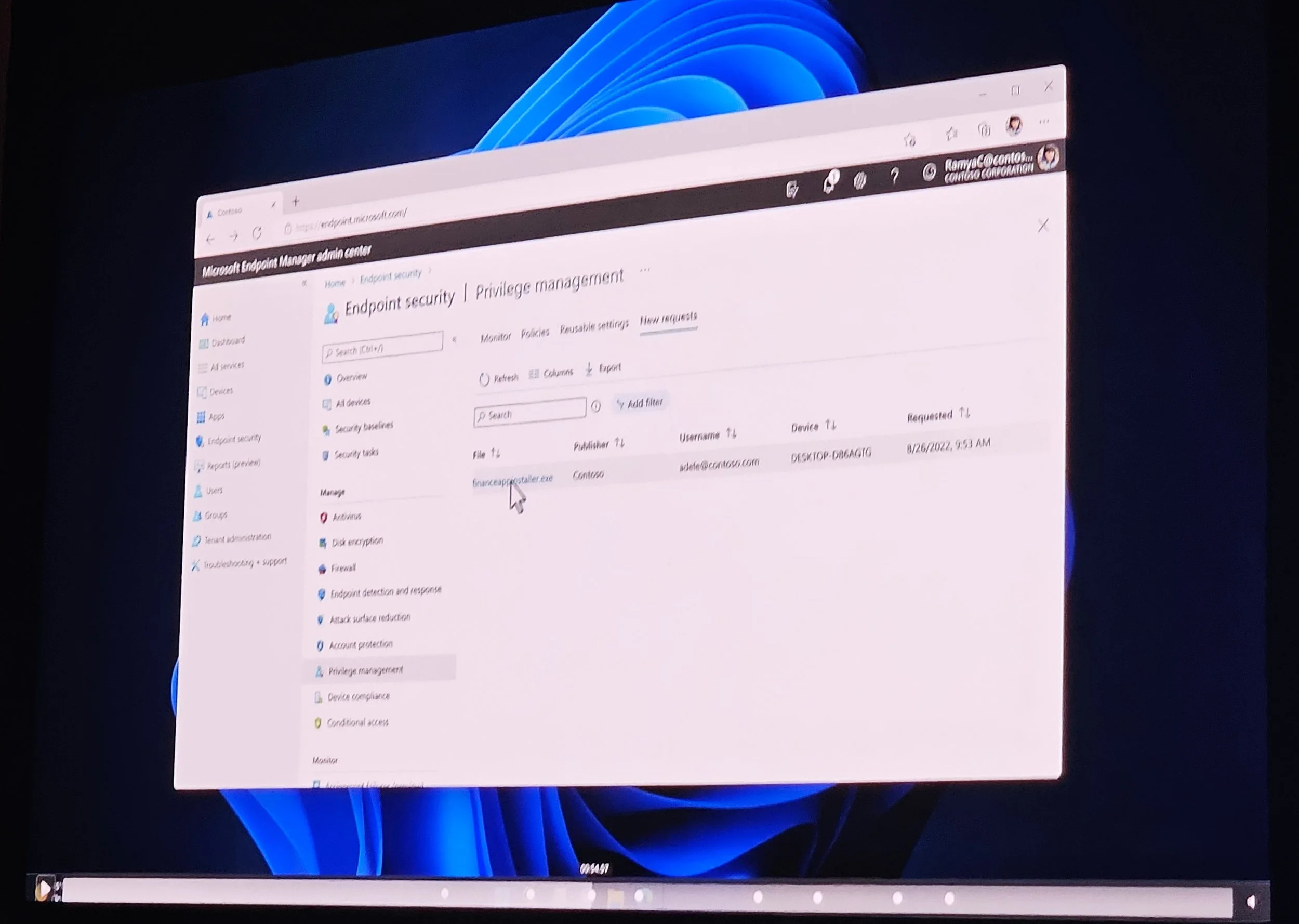
Endpoint Privilege Management (EPM): Admin-approved program installs.
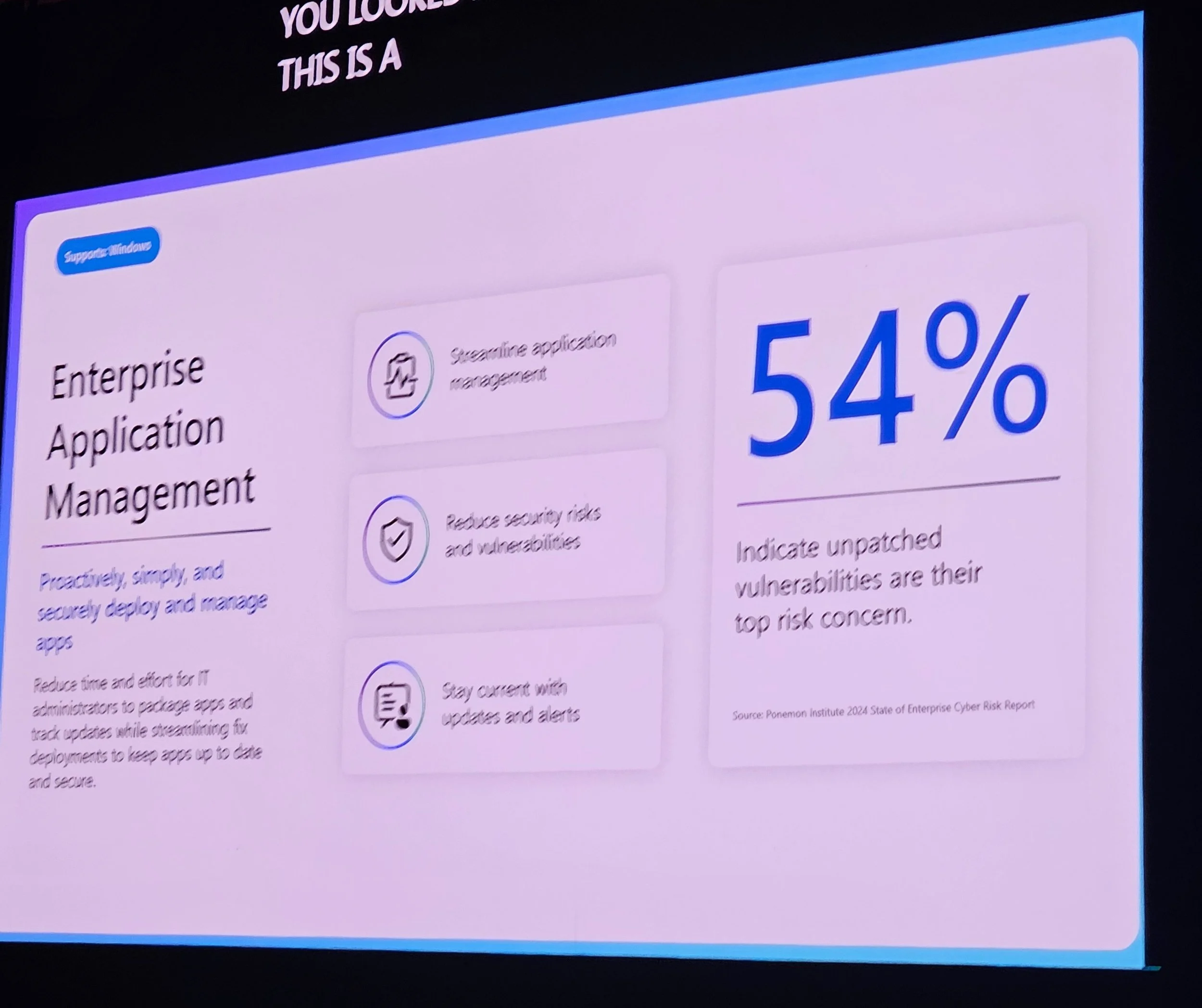
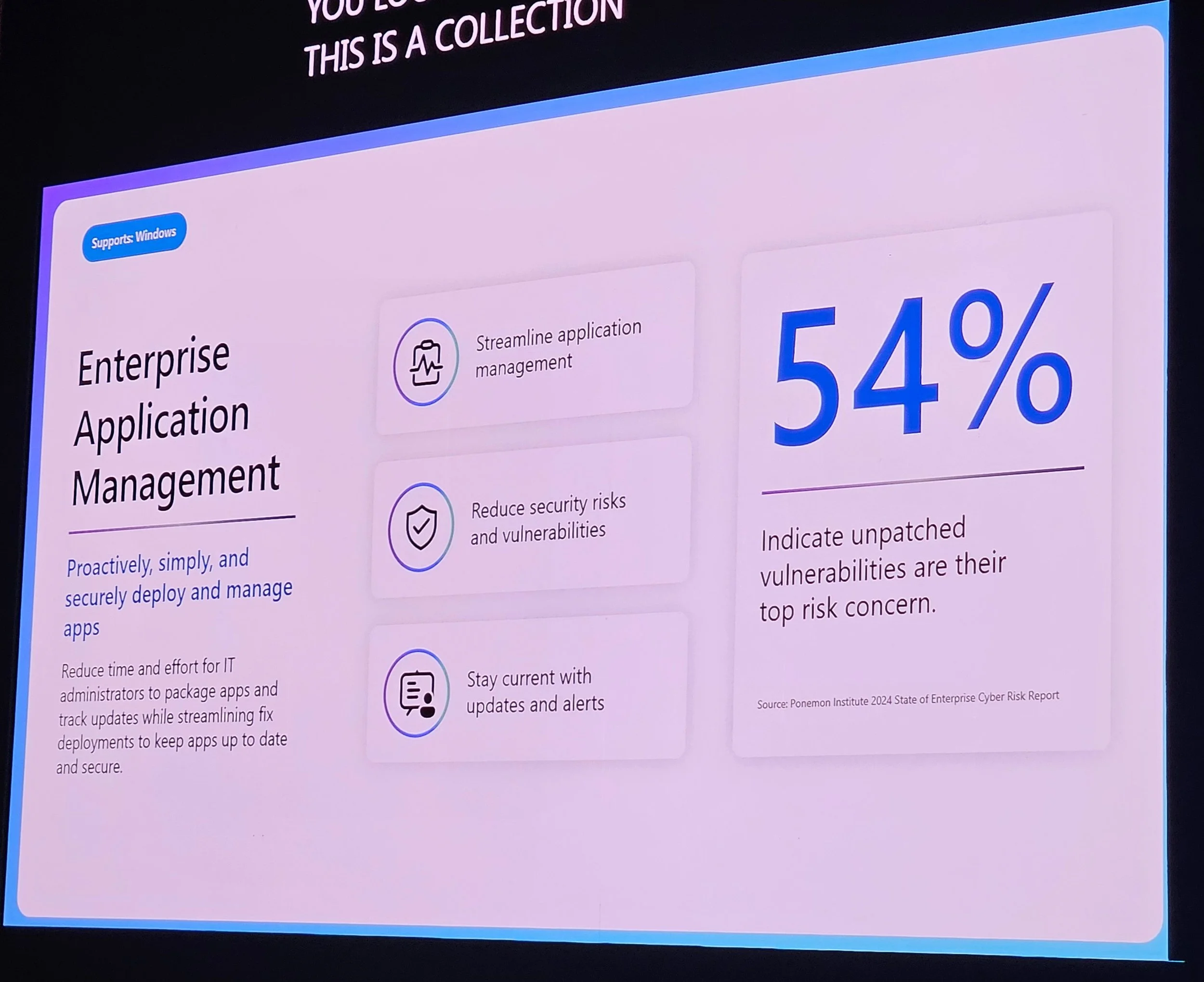
Enterprise App Management (EAM): Now supports PowerShell scripts in packages.
Remote Help: Integrated, unattended support coming.
Advanced analytics: Device timelines, event tracking.
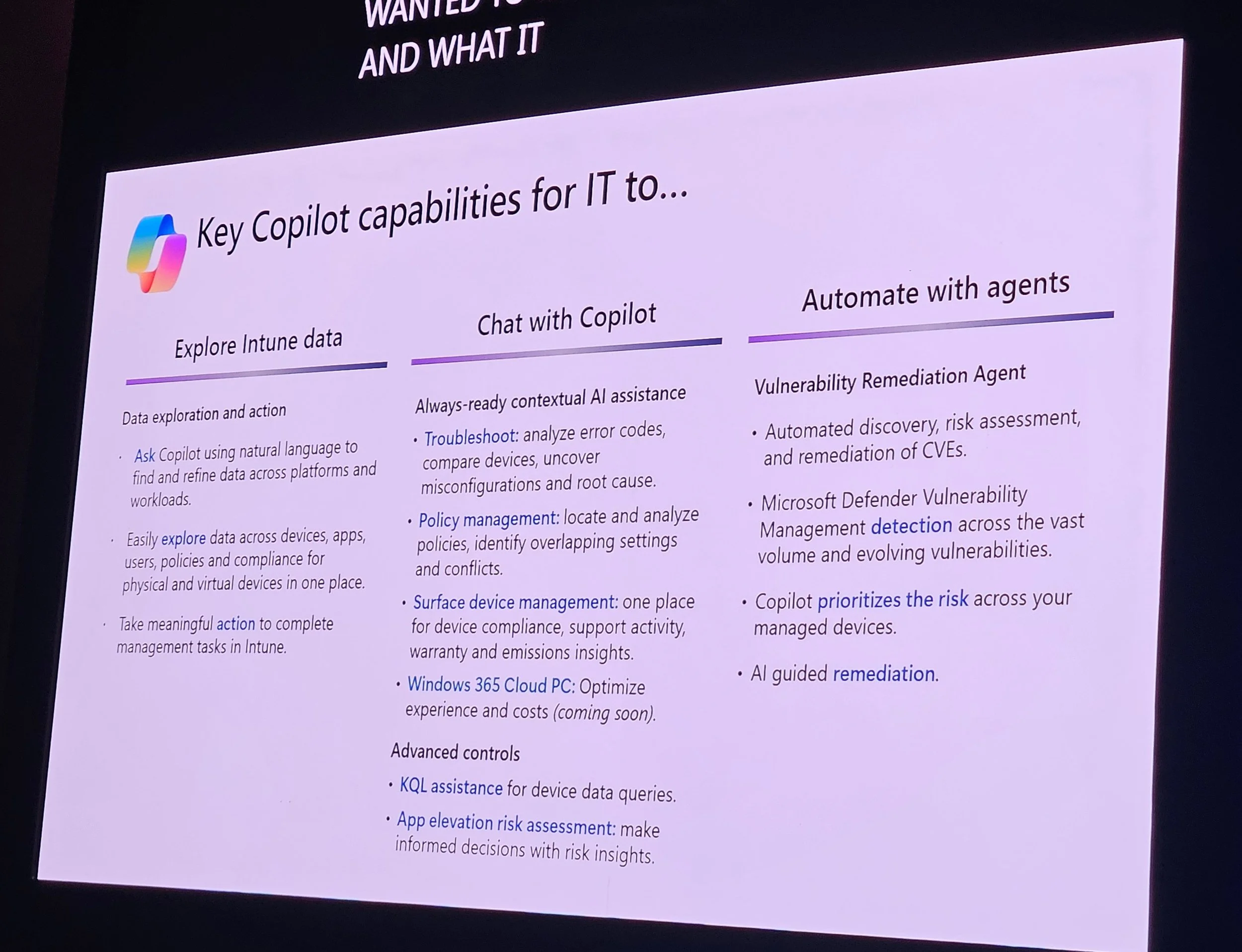
Copilot-assisted device queries (KQL), near real-time data.
Multi-device queries use cached data.
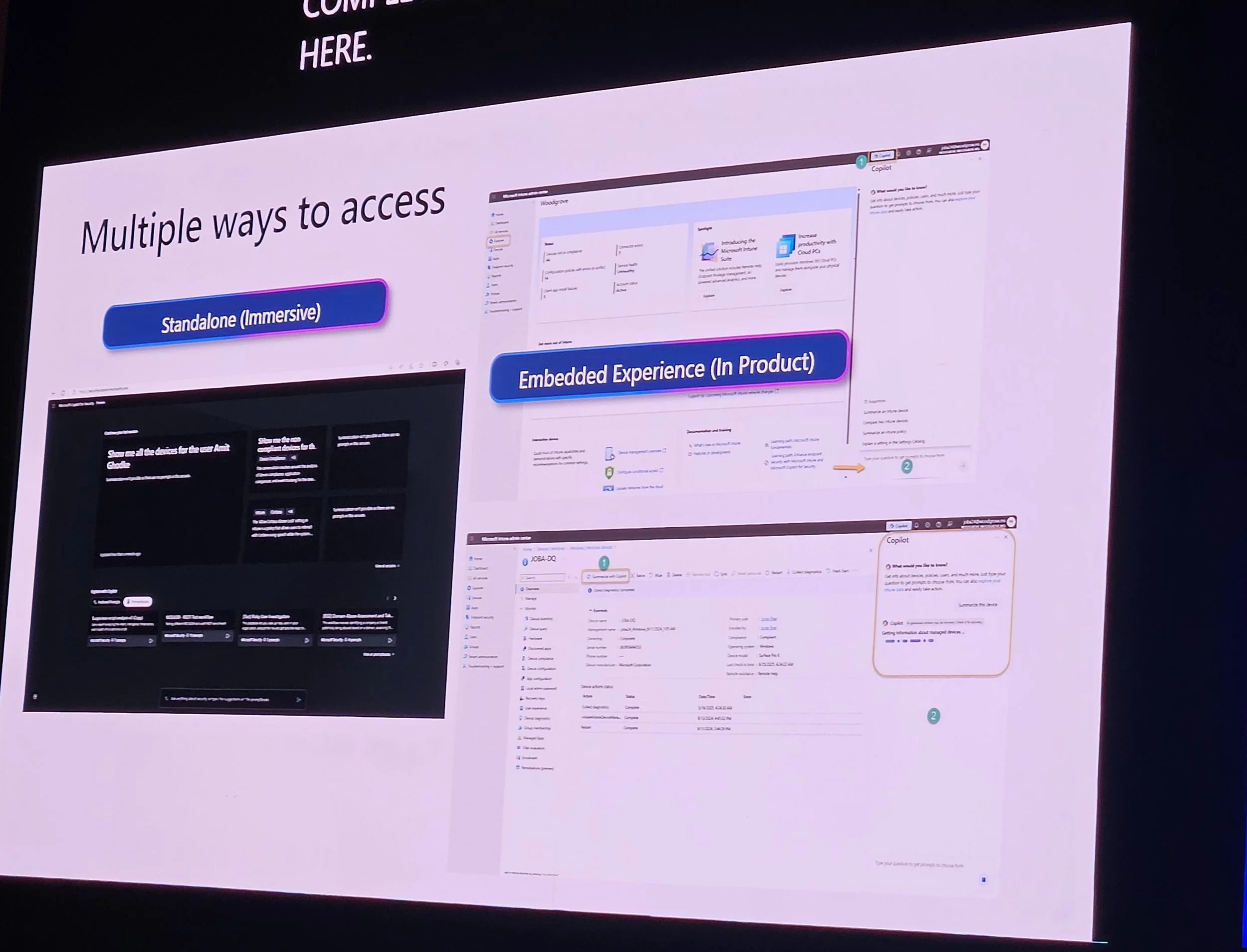
Explorer: Tenant-wide data view, KQL with Copilot assistance.
Vulnerability & remediation agent in Intune (not Defender).
7. Security Best Practices for Windows Cloud
Steve Thomas on security:
Secure identity, access, and data.
Trusted Launch VMs, port 3389 disabled, Credential Guard/HVCI enabled by default.
Passwordless authentication (biometrics, YubiKeys) recommended.
SSPR as backup for passwordless.
Conditional access/user re-authentication policies.
Mobile Application Management (MAM) for iOS/Android/Edge; coming to Windows.
Data protection: MIP (lock), DLP (block).
Watermarking, screen capture protection, clipboard control.
Purview integration: Data protection, customer lockbox, insider risk management, forensic tools.
8. Business Continuity & Disaster Recovery
Linda Zhu on DR/BC:
Point-in-time restore: 10 short-term, 4 long-term, 1 manual snapshot.
End users and IT admins can restore PCs (if policy allows).
Cross-region DR and DR Plus: Add-ons, generally available.
Temporary Cloud PC during outages; returns to normal after.
9. Q&A and Closing Thoughts
Additional sessions and Q&A.
Asked about Copilot in Intune with Security Copilot licensing—response: “Let’s talk later this week.” (Possible announcement coming.)